Attack Tools
Sometimes, the best defense is a good offense. Bishop Fox’s attack tools for Google Hacking level the playing field by allowing our clients to find information disclosures and exposed vulnerabilities before others do. Arm yourself with our arsenal of attack tools that leverage Google, Bing, and other popular search engines.The activity folio contains downloads and links to our best Google Hacking analysis and chargeless aegis tools. Defensive strategies are additionally introduced, including avant-garde solutions that use Google Alerts to adviser your arrangement and systems.
SearchDiggity
SearchDiggity v 3
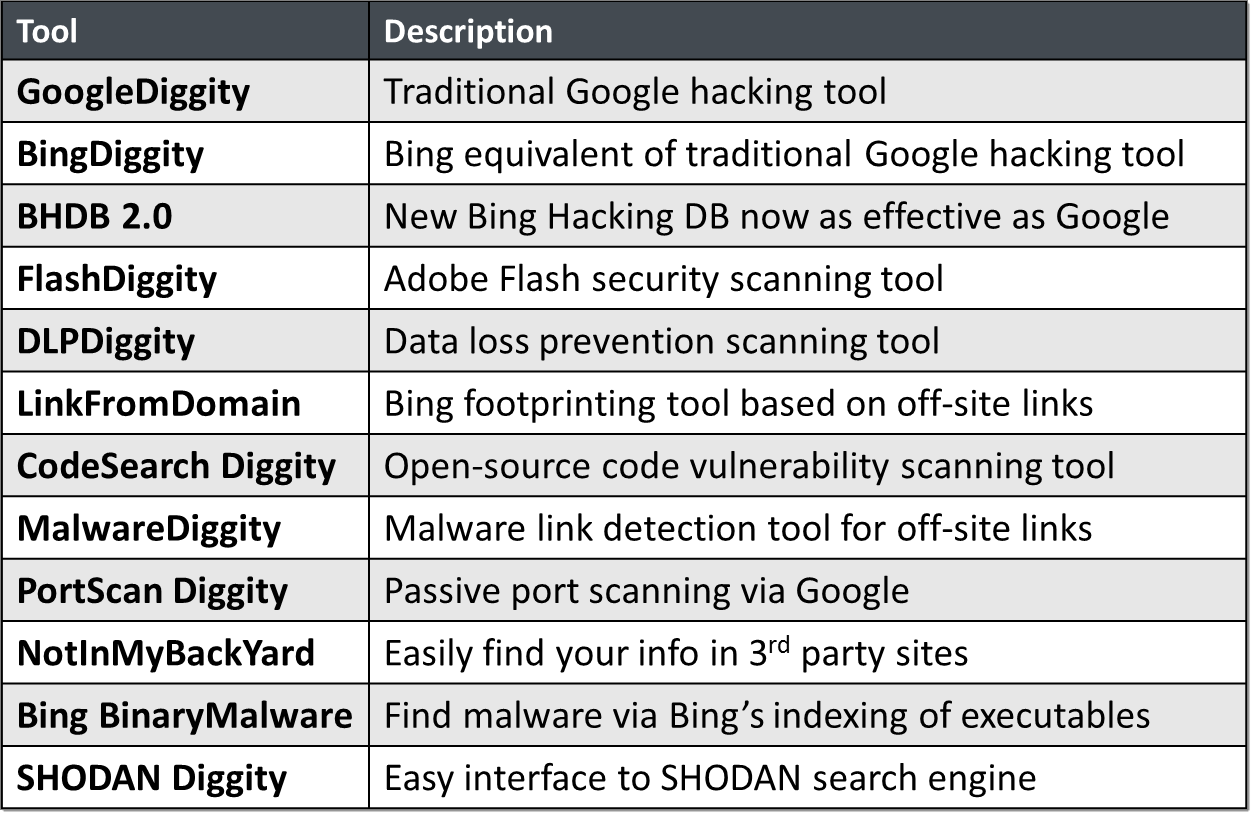
SearchDiggity 3.1 is the primary attack tool of the Google Hacking Diggity Project. It is Bishop Fox’s MS Windows GUI application that serves as a front-end to the most recent versions of our Diggity tools: GoogleDiggity, BingDiggity, Bing LinkFromDomainDiggity, CodeSearchDiggity, DLPDiggity, FlashDiggity, MalwareDiggity, PortScanDiggity, SHODANDiggity, BingBinaryMalwareSearch, and NotInMyBackYard Diggity.
Downloads
| SearchDiggity_v3.1.0.msi |
SearchDiggity - Tool Screenshots
With the retirement of Google’s AJAX Search API on November 1, 2010, most of the security utilities available for Google Hacking cease to function properly, leaving the security industry with a need for new and innovative tools. GoogleDiggity is a new utility designed to help fill that need, now leveraging the Google JSON/ATOM Custom Search API, so it will not get you blocked by Google bot detection while scanning. Also, unlike other Google Hacking tools available, GoogleDiggity actually allows you to specify a Google Custom Search Engine (CSE) id to run Google Hacking vulnerability checks against a customized version of Google that will only return results tailored to your organization. Using the Google Custom Search API, you get 100 queries/day for free, and you get up to 10,000 queries per day pretty cheap ($5 per 1000 Google queries). For more info, see the API’s pricing section. Each query can return a maximum of 100 results per query. In addition to using the official APIs with SearchDiggity, we’ve also implemented scraping of Google and Bing through lists of open web proxies, to prevent being blocked by bot detection mechanisms. This gives the user access to significantly more search results, all for free.
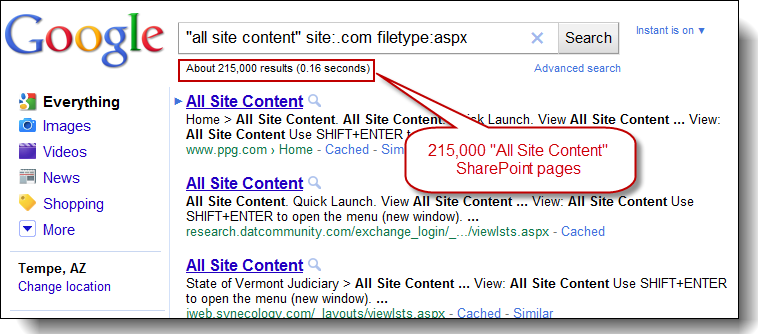
Utilizes Google Code Search to identifies vulnerabilities in open source code projects hosted by Google Code, MS CodePlex, SourceForge, Github, and more. The tool comes with over 130 default searches that identify SQL injection, cross-site scripting (XSS), insecure remote and local file includes, hard-coded passwords, and much more. Essentially, Google CodeSearchDiggity provides a source code security analysis of nearly every single open source code project in existence – simultaneously. NOTE – The Code Search API has been retired by Google as of January 15, 2012. However, the risks associated with information disclosures and vulnerabilities exposed in open-source code remains. As such, we are currently working on an alternative search API to migrate CodeSearchDiggity to in order to identify vulnerabilities in open-source code projects.
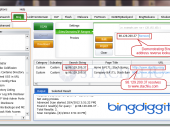
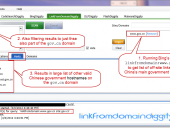
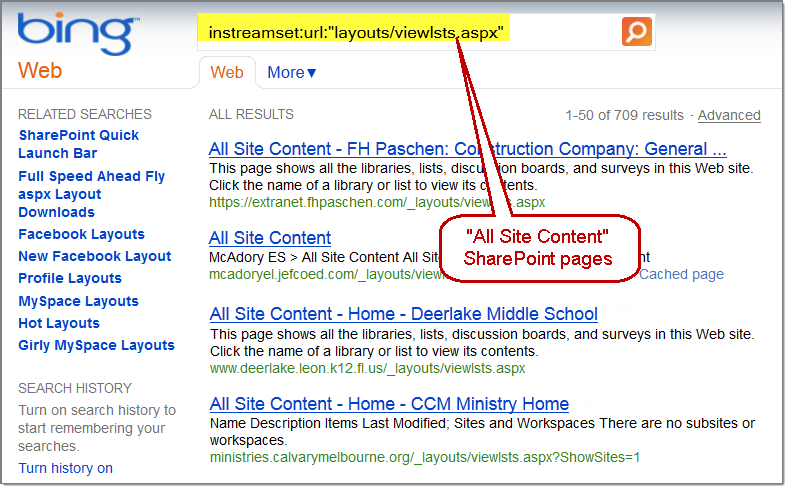
Leverages the new Bing Search API (Windows Azure Marketplace) and Stach & Liu’s newly developed Bing Hacking Database v2.0 (BHDBv2.0) to find vulnerabilities and sensitive information disclosures related to your organization that are exposed via Microsoft’s Bing search engine. This utility also provides footprinting functionality that allows you to enumerate URLS, hosts, domains, IP-to-virtual host mappings, etc. for target companies. Exploiting recent API changes and undocumented features within Bing, we’ve been able to completely overcome the previous Bing hacking limitations (such as the disabling of the inurl:, link: and linkdomain: search operators) to create an entirely new BHDB v2.0 that makes Bing hacking just as effective as Google hacking (if not more so) for uncovering vulnerabilities and data leaks on the web. For example, Bing now has ability to use the ext: search operator, which previously didn’t exist. Bing also now has the ability to mimic Google’s inurl: search operator by using Bing’s instreamset:url: search operator. The BHDB v2.0 also includes an entirely new SharePoint Bing Hacking database, containing attack strings targeting Microsoft SharePoint deployments via Bing. As of August 1, 2012, the Bing Search API has moved to the Windows Azure Marketplace – a one stop shop for data sets, cloud applications and analysis tools. Available for free up to 5,000 queries per month. Maximum of 50 results per query. In addition to using the official APIs with SearchDiggity, we’ve also implemented scraping of Google and Bing through lists of open web proxies, to prevent being blocked by bot detection mechanisms. This gives the user access to significantly more search results, all for free.
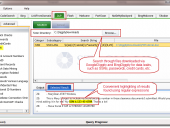
Data loss prevention tool that leverages Google/Bing to identify exposures of sensitive information (e.g. SSNs, credit card numbers, etc.) via common document formats such as .doc, .xls, and .pdf. DLPDiggity utilizes IFilters to search through the actual contents of files, as opposed to just the meta-data. Using .NET regular expressions, DLPDiggity can find almost any type of sensitive data within common document file formats.
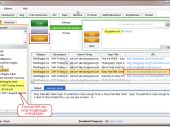
Automates Google searching/downloading/decompiling/analysis of SWF files to identify Flash vulnerabilities and information disclosures. FlashDiggity first leverages the GoogleDiggity tool in order to identify Adobe Flash SWF applications for target domains via Google searches, such as ext:swf. Next, the tool is used to download all of the SWF files in bulk for analysis. The SWF files are disassembled back to their original ActionScript source code, and then analyzed for code-based vulnerabilities.
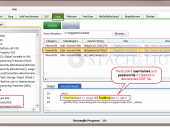
Automates Google searching/downloading/decompiling/analysis of SWF files to identify Flash vulnerabilities and information disclosures. FlashDiggity first leverages the GoogleDiggity tool in order to identify Adobe Flash SWF applications for target domains via Google searches, such as ext:swf. Next, the tool is used to download all of the SWF files in bulk for analysis. The SWF files are disassembled back to their original ActionScript source code, and then analyzed for code-based vulnerabilities.
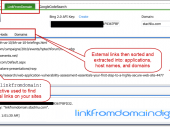
Leverages the Bing 2.0 API and the Google Safe Browsing API together to provide an answer to a simple question, “Am I being used as a platform to distribute malware to people who visit my website?” MalwareDiggity first identifies off-site links of your web sites using Bing’s linkfromdomain: search directive, and then tests to see if those off-site links are to known malware distribution sites by running them against Google’s Safe Browsing API.
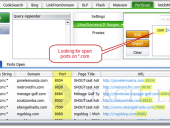
How would you like to get Google to do your port scanning for you? Using undocumented functionality within Google, we’ve been able to turn Google into an extremely effective network port scanning tool. As an example, see the Google search results for administrative web applications listening on non-standard TCP ports for the com domain. You can provide domains, hostnames, and even IP address ranges to scan in order to identify open ports ranging across all 65,535 TCP ports. An additional benefit is that this port scanning is completely passive – no need to directly communicate with target networks since Google has already performed the scanning for you.
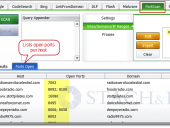
How would you like to get Google to do your port scanning for you? Using undocumented functionality within Google, we’ve been able to turn Google into an extremely effective network port scanning tool. As an example, see the Google search results for administrative web applications listening on non-standard TCP ports for the com domain. You can provide domains, hostnames, and even IP address ranges to scan in order to identify open ports ranging across all 65,535 TCP ports. An additional benefit is that this port scanning is completely passive – no need to directly communicate with target networks since Google has already performed the scanning for you.
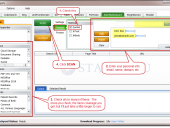
Don’t be the last to know if LulzSec or Anonymous post data dumps of your company’s passwords on PasteBin.com, or if a reckless employee shares an Excel spreadsheet with all of your customer data on a public website. NotInMyBackYard leverages both Google and Bing, and comes with pre-built queries that make it easy for users to find sensitive data leaks related to their organizations that exist on 3rd party sites, such as PasteBin, YouTube, and Twitter. Uncover data leaks in documents on popular cloud storage sites like Dropbox, Microsoft SkyDrive, and Google Docs. A must have for organizations that have sensitive data leaks on domains they don’t control or operate.
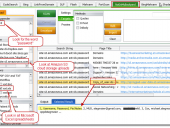
Don’t be the last to know if LulzSec or Anonymous post data dumps of your company’s passwords on PasteBin.com, or if a reckless employee shares an Excel spreadsheet with all of your customer data on a public website. NotInMyBackYard leverages both Google and Bing, and comes with pre-built queries that make it easy for users to find sensitive data leaks related to their organizations that exist on 3rd party sites, such as PasteBin, YouTube, and Twitter. Uncover data leaks in documents on popular cloud storage sites like Dropbox, Microsoft SkyDrive, and Google Docs. A must have for organizations that have sensitive data leaks on domains they don’t control or operate.
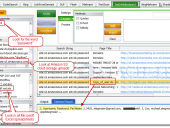
Don’t be the last to know if LulzSec or Anonymous post data dumps of your company’s passwords on PasteBin.com, or if a reckless employee shares an Excel spreadsheet with all of your customer data on a public website. NotInMyBackYard leverages both Google and Bing, and comes with pre-built queries that make it easy for users to find sensitive data leaks related to their organizations that exist on 3rd party sites, such as PasteBin, YouTube, and Twitter. Uncover data leaks in documents on popular cloud storage sites like Dropbox, Microsoft SkyDrive, and Google Docs. A must have for organizations that have sensitive data leaks on domains they don’t control or operate.
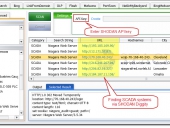
SHODAN Diggity provides an easy-to-use scanning interface to the popular SHODAN hacking search engine, and comes equipped with convenient list of 167 search queries ready in a pre-made dictionary file, known as the SHODAN Hacking Database (SHDB). SHODAN is a search engine that lets you find specific types of computers (routers, servers, etc.) using a variety of filters. Some have also described it as a search engine of service banners. Shodan collects data mostly on web servers at the moment (port 80), but there is also some data from FTP (21), SSH (22) and Telnet (23) services. Web search engines, such as Google and Bing, are great for finding websites. But what if you’re interested in finding computers running a certain piece of software (such as Apache)? Or you want to see how many anonymous FTP servers there are? Maybe a new vulnerability came out and you want to see how many hosts it could infect? Traditional web search engines don’t let you answer those questions.
See media gallery for more.
Hacking Dictionaries
Bing Hacking Database - BHDB v2
 Exploiting recent API changes and undocumented features within Bing, we’ve been able to completely overcome the previous Bing hacking limitations (such as the;disabling of the inurl:, link: and linkdomain: search operators) to create an entirely new BHDB v2.0 that makes Bing hacking just as effective as Google hacking (if not more so) for uncovering vulnerabilities and data leaks on the web.
Exploiting recent API changes and undocumented features within Bing, we’ve been able to completely overcome the previous Bing hacking limitations (such as the;disabling of the inurl:, link: and linkdomain: search operators) to create an entirely new BHDB v2.0 that makes Bing hacking just as effective as Google hacking (if not more so) for uncovering vulnerabilities and data leaks on the web.
For example, Bing now has ability to use the ext: search operator, which previously didn’t exist. Bing also now has the ability to mimic Google’s inurl: search operator by using Bing’s instreamset:url: search operator.
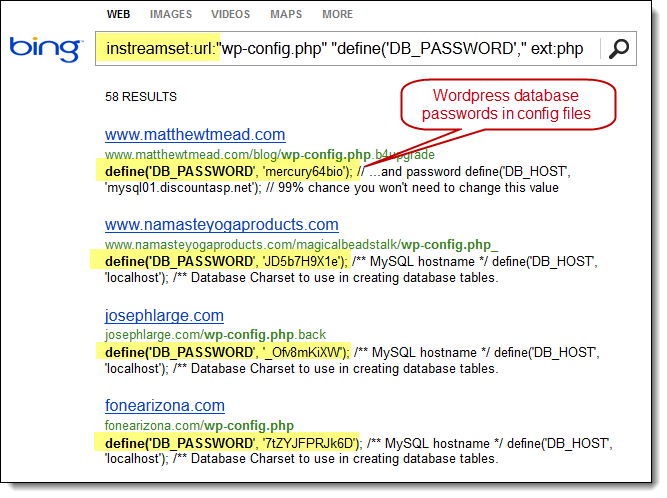
The BHDB v2.0 also includes an entirely new SharePoint Bing Hacking database, containing attack strings targeting Microsoft SharePoint deployments via Bing.
Downloads
| Bing Hacking Database (BHDB) v2.0.txt |
GHDB Reborn Dictionaries - Exploit-DB
The good folks over at Exploit-DB.com were kind enough to pick up where Johnny Long left off and resurrect the GHDB. They now maintain an updated version of the GHDB in a project labeled Google Hacking Database Reborn.
In that same spirit, we at the Diggity project were kind enough to translate their efforts into GoogleDiggity compatible input text files. These dorks are included with the standard SearchDiggity dictionary set, and can also be downloaded below.
SHODAN Hacking Database - SHDB
 The new SHODAN Hacking Database (SHDB) input dictionary file containing 167 queries that allow users to uncover interesting information via the SHODAN search engine. This dictionary helps target various technologies including webcams, printers, VoIP devices, routers, switches, and even SCADA/Industrial Control Systems (ICS) just to name a few. This dictionary comes preloaded with SHODAN Diggity (part of the SearchDiggity attack tool suite), which provides an easy-to-use scanning interface to the popular SHODAN hacking search engine, using the SHODAN API.
The new SHODAN Hacking Database (SHDB) input dictionary file containing 167 queries that allow users to uncover interesting information via the SHODAN search engine. This dictionary helps target various technologies including webcams, printers, VoIP devices, routers, switches, and even SCADA/Industrial Control Systems (ICS) just to name a few. This dictionary comes preloaded with SHODAN Diggity (part of the SearchDiggity attack tool suite), which provides an easy-to-use scanning interface to the popular SHODAN hacking search engine, using the SHODAN API.
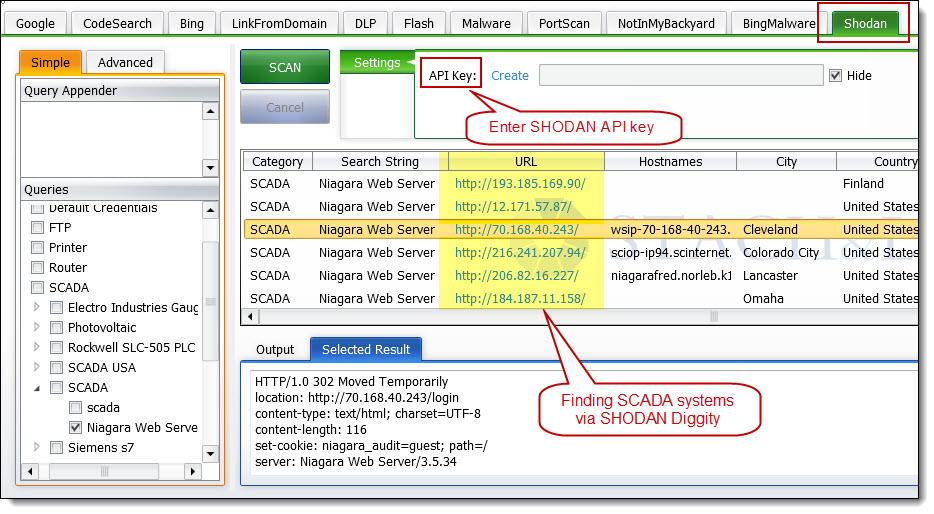
SHODAN is a search engine that lets you find specific types of computers (routers, servers, etc.) using a variety of filters. Some have also described it as a search engine of service banners. Shodan collects data mostly on web servers at the moment (port 80), but there is also some data from FTP (21), SSH (22) and Telnet (23) services.
Web search engines, such as Google and Bing, are great for finding websites. But what if you’re interested in finding computers running a certain piece of software (such as Apache)? Or you want to see how many anonymous FTP servers there are? Maybe a new vulnerability came out and you want to see how many hosts it could infect? Traditional web search engines don’t let you answer those questions.
Downloads
| SHODAN Hacking Database (SHDB).txt |
Hacking Google Custom Search
Hacking CSE for All Top Level Domains
Previously, the Google Diggity hacking tools provided an extra bonus feature of allowing you to specify a Google Custom Search Engine (CSE) id to have search queries performed against a custom Google engine of your creation.
With the retirement of the Google AJAX API announced on November 1, 2010, we’ve since migrated our Google Diggity tools to the new Google JSON/ATOM Custom Search API. With this new API, utilizing Google Custom Search Engines is now a requirement, and not just a bonus add-on feature.
Another way to go is to use this document, which provides a quick overview of how you can create a Google CSE of your own that simulates getting the normal full results of Google (i.e. search results across the whole Internet). We accomplish this by creating a Google CSE that returns results for all top level domains (TLDs) – examples: .com, .org. .gov, .edu, …
Bypassing Google CSE to get Full Web Search Results
Wouldn’t it be nice to go through the Google Custom Search API, but still get the full Google results for the entire Internet (i.e. not filtered results)? You can! Bypass using an exclamation point before any valid Google CSE id value, try: !001280586187183383443:vcqkedkugeo