
This blog post was authored by Senior Security Analyst Zach Julian; you can connect with him on Twitter here.
In the first week of 2017, Iranian ISP Telecommunication Infrastructure Company (TIC) performed a BGP hijack affecting 99.192.226.0/24. Their goal was to censor select websites residing on the /24 block from Iranian internet users. However, the BGP hijack leaked on to the greater internet, resulting in the IP range becoming inaccessible to users outside of Iran, including from India, Russia, Indonesia, and Hong Kong [1].
In this blog post, I’ll show how the attack began, propagated, and was finally countered. Readers unfamiliar with BGP hijacking should refer to “An Overview of BGP Hijacking."
We can analyze this event using RIPE NCC’s BGPlay, a tool for visualizing BGP routing information.
Start and Spread of the Attack
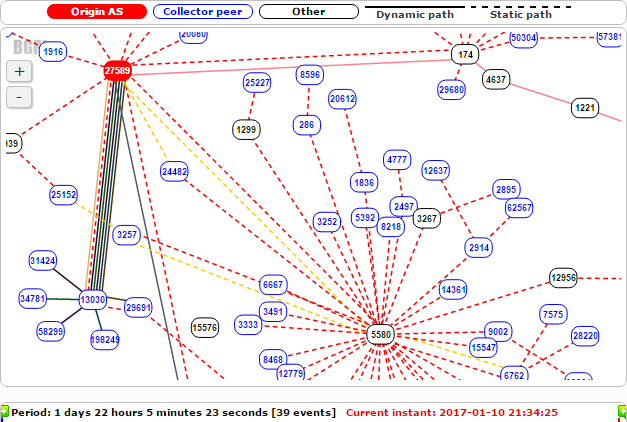
99.192.226.0/17, which contains victim subnet 99.192.226.0/24, is announced from MojoHost-operated Autonomous System 27589. Below, we can see typical paths when traffic to 99.192.226.0/17 is routing properly. At this point, the legitimate origin AS27589, marked in red, is peered with AS13030, AS5580, and AS174, among others:
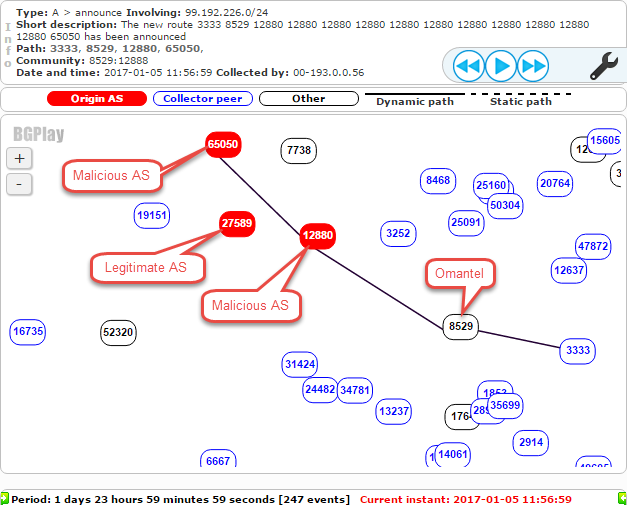
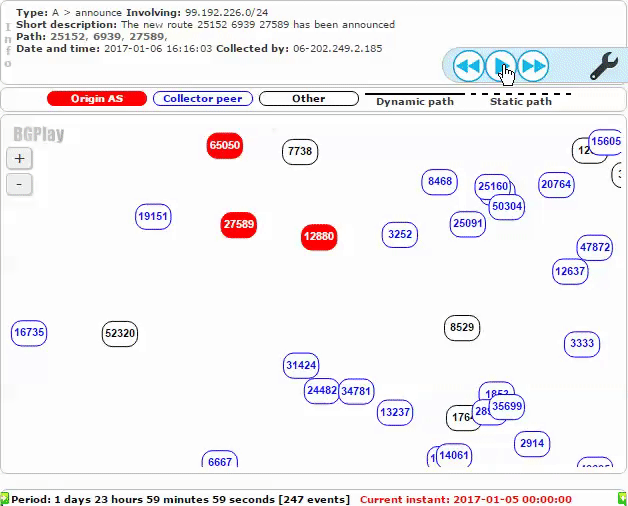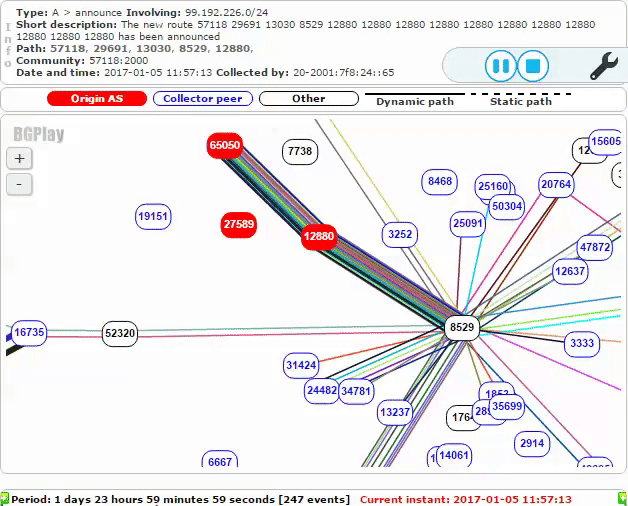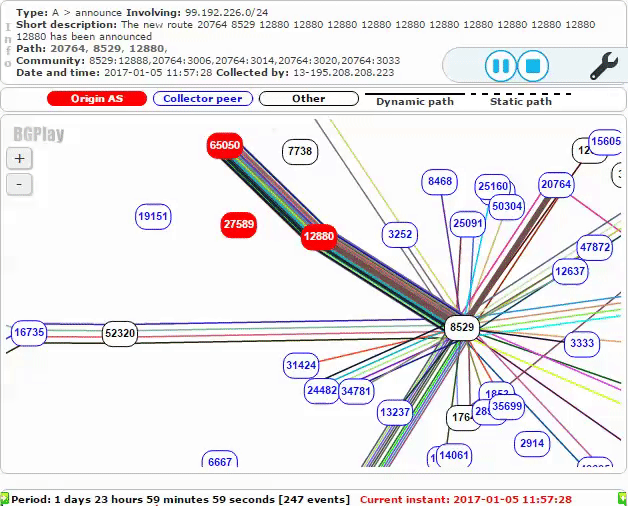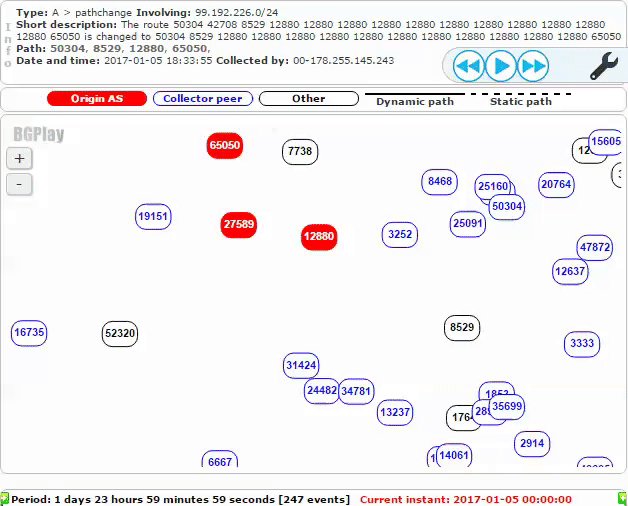
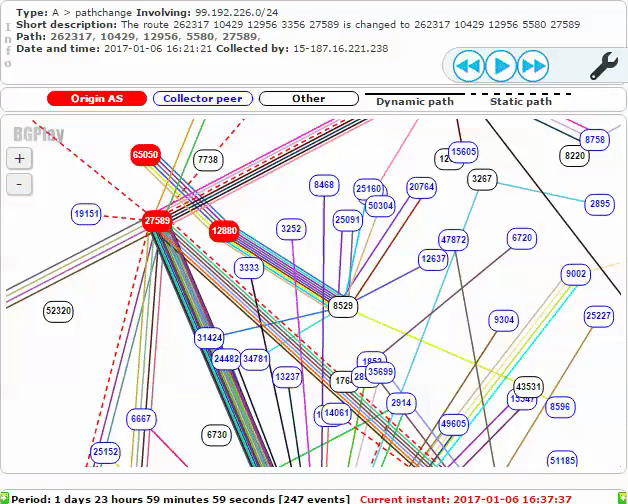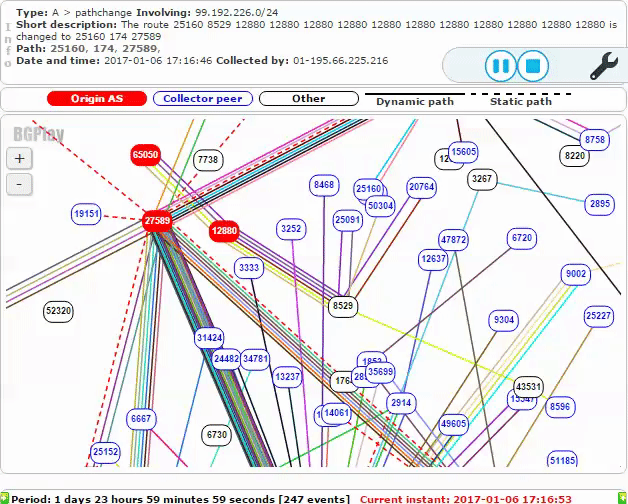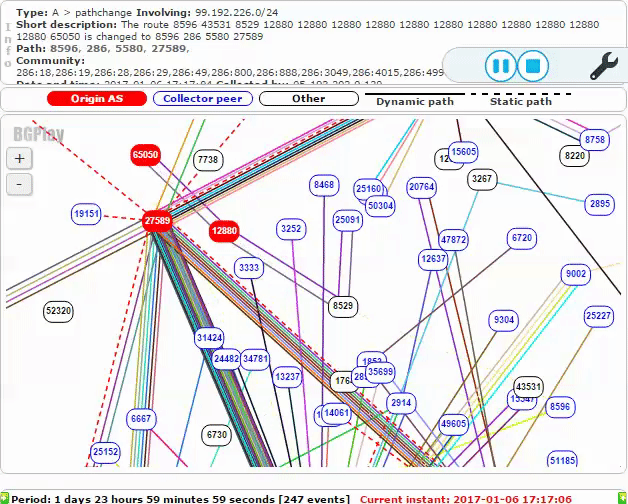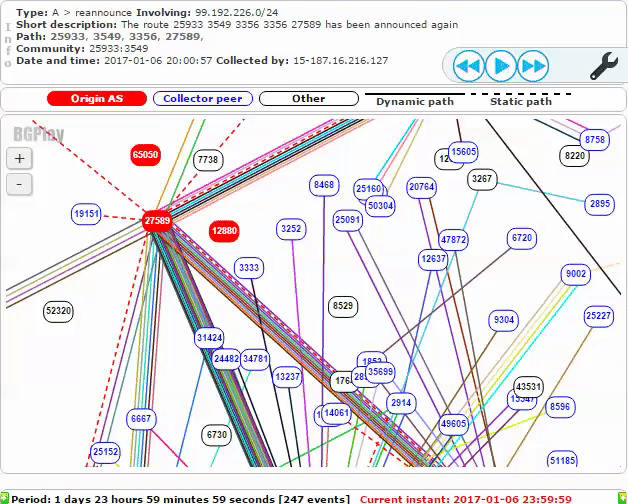
Around 12:00 UTC (15:30 Iran time) on Thursday, January 5th, AS12880 (TIC) and AS65050 (Private ASN) began making malicious route announcements for 99.192.226.0/24. Because 99.192.226.0/24 is more specific than the prefix AS27589 typically advertises, 99.192.128.0/17, other routers will prefer this path, making it advantageous for BGP hijacking. Shortly after, this route was propagated to AS8529, Omantel, as shown below:
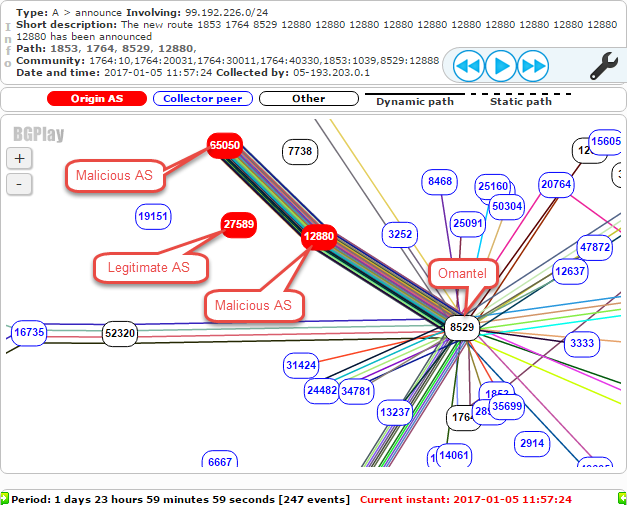
Omantel AS8529 then advertised the malicious route to its peers, resulting in the bogus route affecting more and more of the Internet. The screenshot below shows additional malicious routes announced to other Autonomous Systems a short time later.
The below animation shows new malicious routes being propagated:
How the Attack Was Stopped
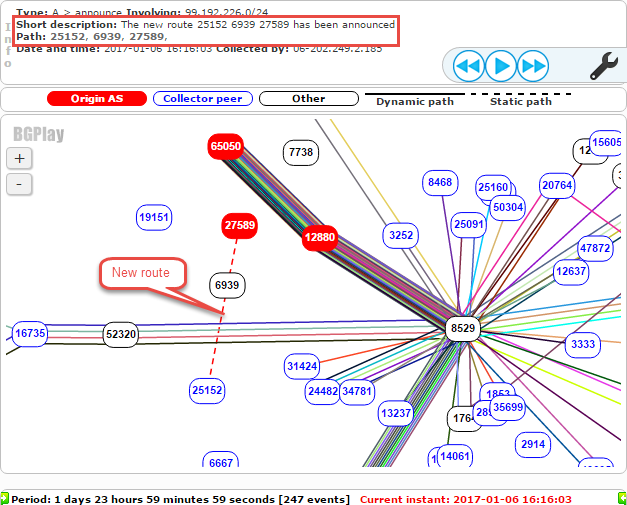
The attack continued until about 16:00 UTC on Friday, January 6th, when two steps were taken to end the hijacking. First, the legitimate AS27589 began making an announcement for 99.192.226.0/24. A static route was configured between AS27589 (MojoHost) and AS25152 (RIPE NCC), which the DNS K-root server belongs to. The new route can be seen below:
Shortly thereafter, AS8529 (Omantel) ceased announcing the malicious route to its peers. After about an hour, AS27589 was back in control of 99.192.226.0/24. As shown below, the BGP routes for that prefix change from AS12880 and AS65050 to the legitimate AS27589:
This incident is another example of BGP’s technical limitations being exploited to restrict internet access. It’s also a unique instance of one country’s laws spilling outside their jurisdiction.
To protect their respective IP space, providers should consider implementing RPKI.
[1] http://www.theverge.com/2017/1/7/14195118/iran-porn-block-censorship-overflow-bgp-hijack
[2] https://dyn.com/blog/iran-leaks-censorship-via-bgp-hijacks/
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.



