Attack Tools
Practical guide to RFID hacking for penetration testers. Investigates the latest attack tools and techniques available for stealing and using RFID proximity badge information to gain unauthorized access to buildings and other secure areas.
RFID Hacking Tools
Tastic RFID Thief
The Tastic RFID Thief is a silent, long-range RFID reader that can steal the proximity badge information from an unsuspecting employee as they physically walk near this concealed device. Specifically, it is targeting 125KHz, low frequency RFID badge systems used for physical security, such as those used in HID Prox and Indala Prox products. Alternatively, the PCB could even be used to weaponize a 13.56MHz, high frequency RFID reader, like those for HID iCLASS access control systems.
Our goal is to make it easy for security professionals to re-create this tool so that they can perform RFID physical penetration tests and better demonstrate the risks posed by these technologies to their management. The hope is that they can get up and running quickly, even if they don’t have an RFID or electrical engineering background.
Downloads of the code, parts list, and PCB designs can be found below, all of which are free for download and use.
Design
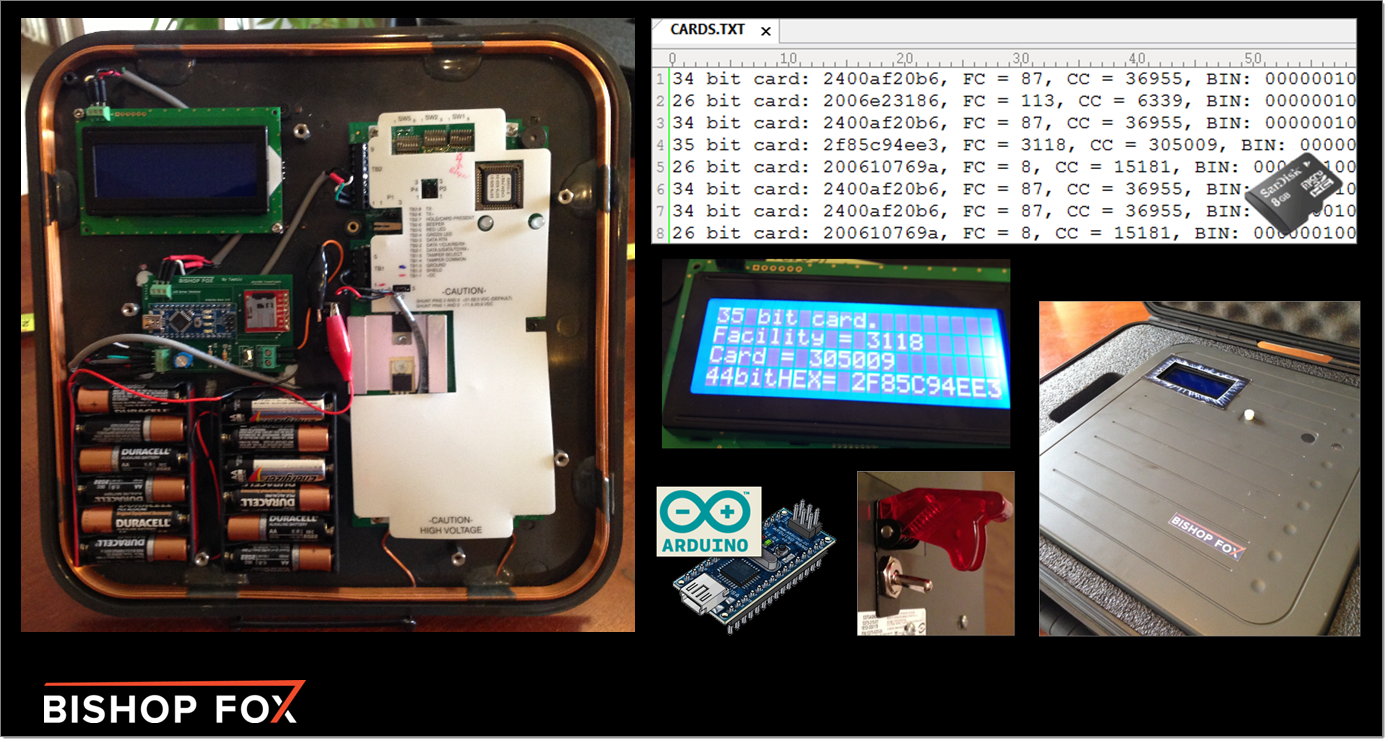
We used an Arduino microcontroller to weaponize a commercial RFID badge reader (the HID MaxiProx 5375 – bought on eBay) – effectively turning it into a custom, long-range RFID hacking tool. This involved the creation of a small, portable PCB (designed in Fritzing) that can be inserted into almost any commercial RFID reader to steal badge info.
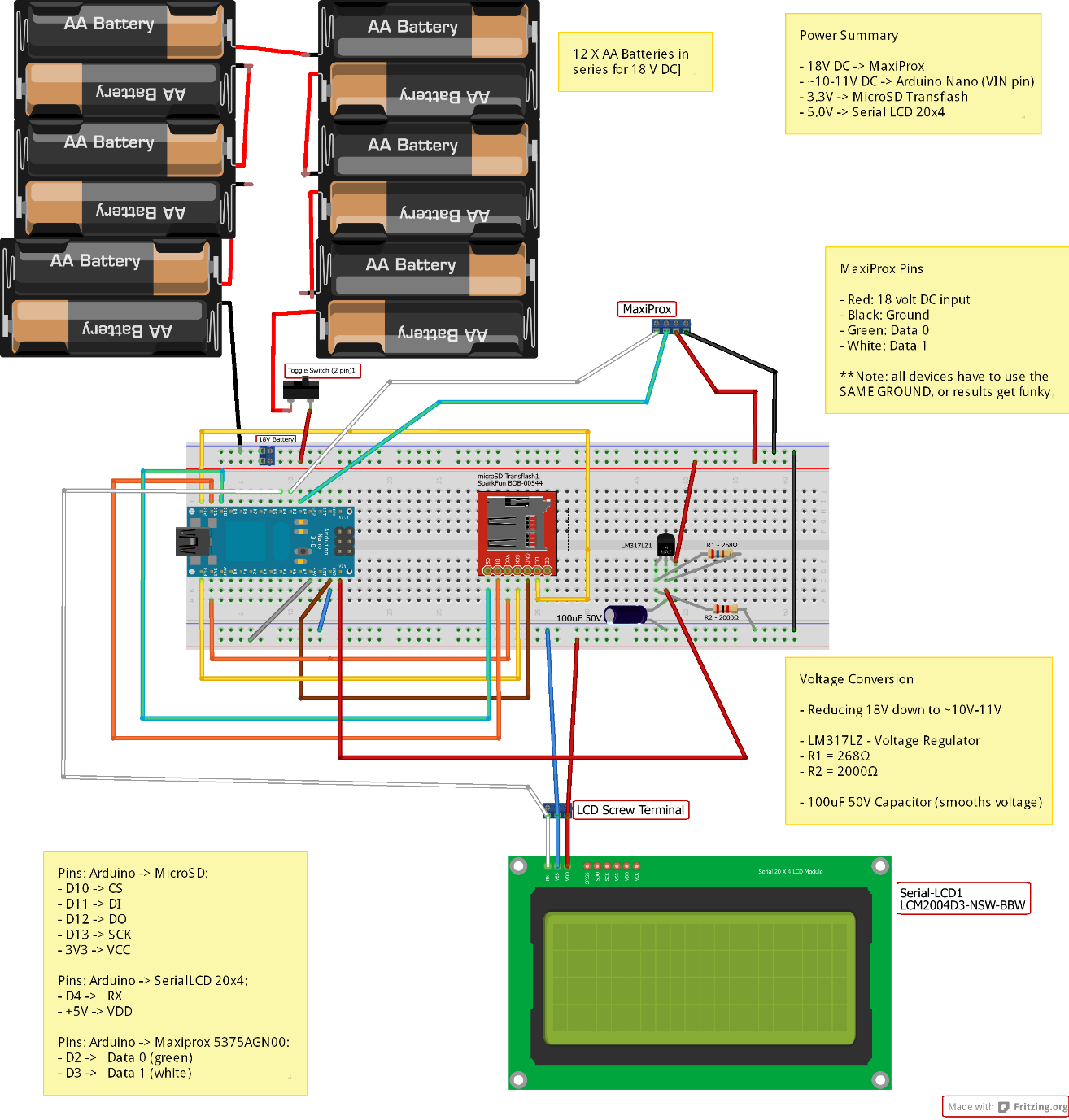
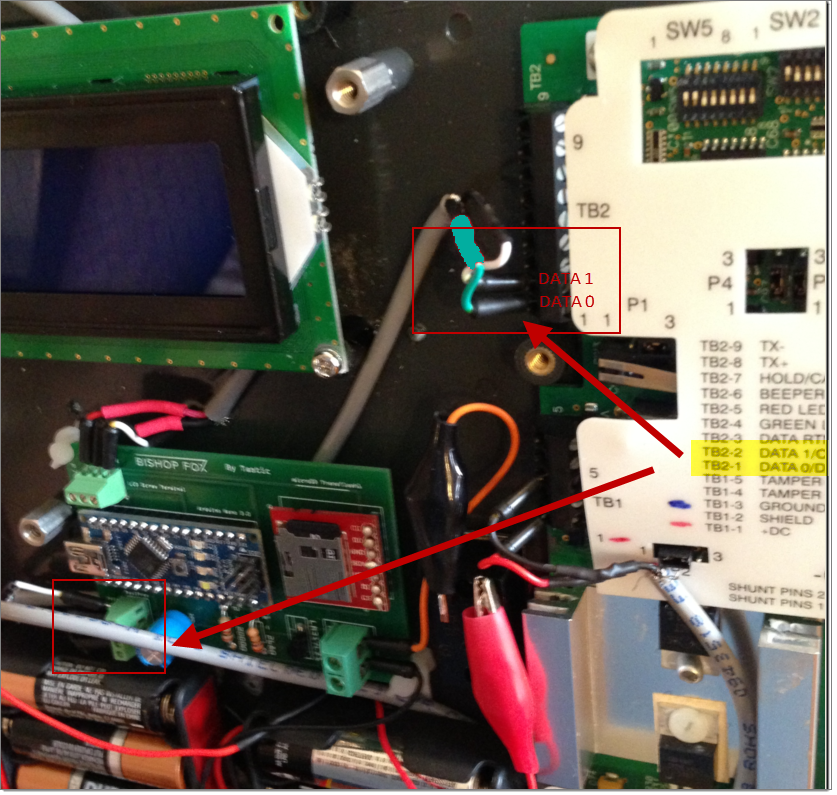
Note, this PCB can alternatively be inserted into an Indala reader for testing Indala Prox deployments (e.g. Indala Long-Range Reader 620). Alternatively, the PCB could even be used to weaponize a high frequency (13.56MHz) RFID reader, such as the iClass R90 Long Range reader. The PCB can be inserted into any RFID reader that supports the standard Wiegand DATA0/DATA1 output (which is pretty much all of them).
The tool steals badge information silently, and conveniently saves it to a text file (CARDS.txt) on a microSD card for later use such as badge cloning.
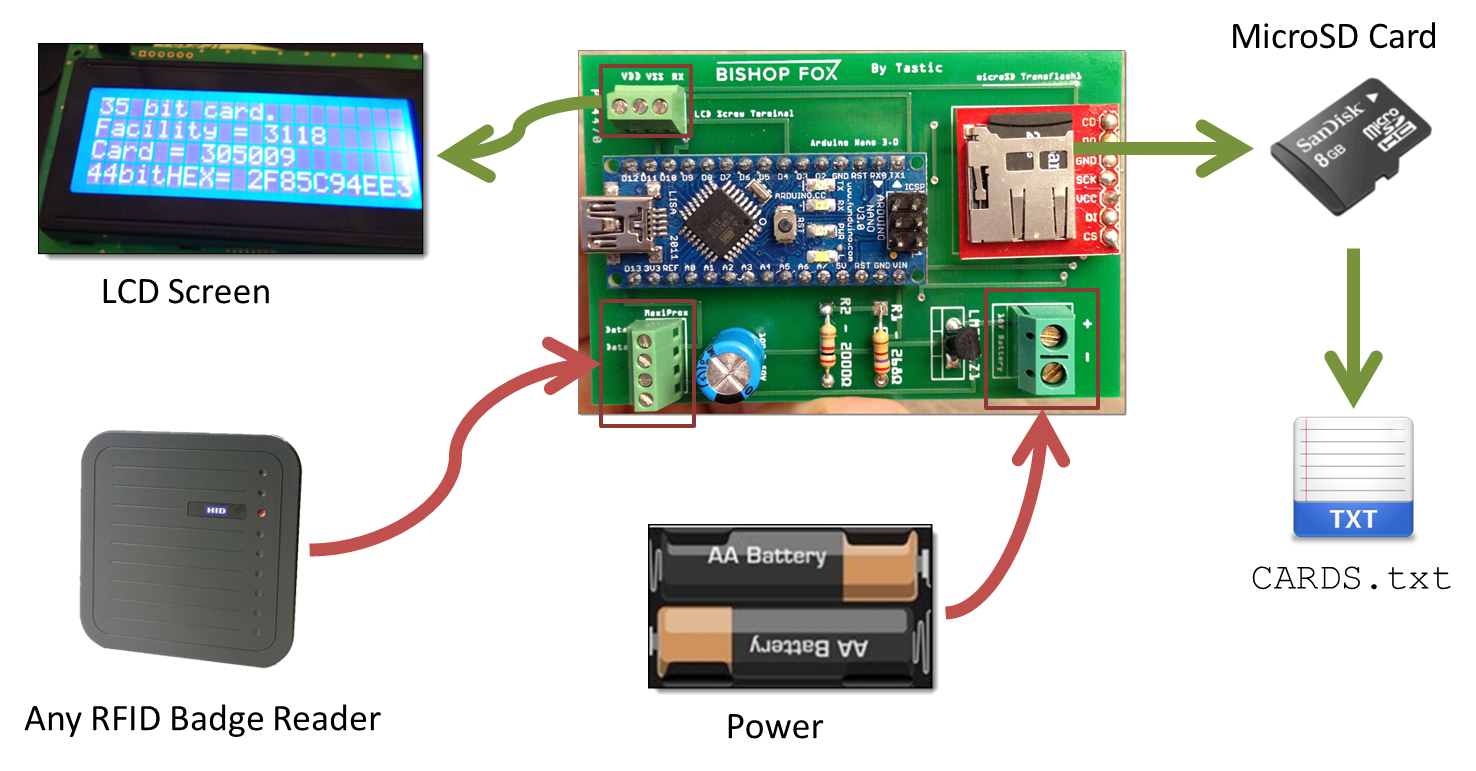
This solution allowed us to read proximity cards from up to 3 feet away, making the stealthy approach an actual reality. A typical attack would involve placing the weaponized reader into a messenger bag or backpack, walking by someone in line at the local Starbucks, and capturing the RFID badge info on their person. A visualization of what the attack would look like is captured in the image below:

You can use the Tastic RFID Thief’s PCB files in the Tastic RFID – PCB Design.zip from the Downloads section below to have a nice PCB printed cheaply at any major site that prints custom boards. A couple cheap pcb printers I’d recommend :
- 4pcb.com: ~$30 for 1 board with student discount:
- Fritzing Fab: ~30 Euro per board
Videos
The short tutorial videos below show the Tastic RFID Thief in action:
Mr. Robot featured the Tastic RFID Thief tool, as detailed by Rolling Stone’s article on their best hacks:
- Mr. Robot: Episodes featuring the Tastic RFID Thief:
Long Range Readers to Weaponize
The table below provides links to the 3 long range RFID readers sold by HID Global, that can be weaponized by the Tastic RFID Thief PCB. You can typically find all 3 available for purchase on eBay.
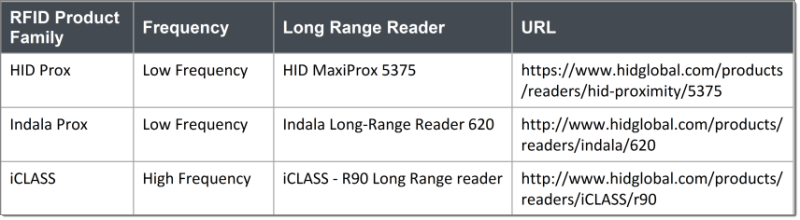
Tastic RFID Thief’s PCB can be inserted into almost any commercial RFID badge reader. It has been successfully tested with the long-range readers sold by HID Global for 3 of their 4 major RFID product families.
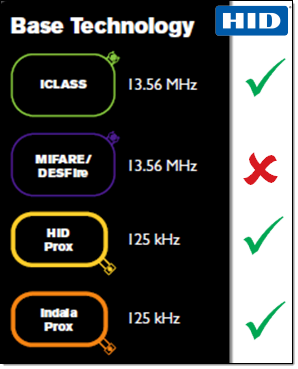
For the Black Hat USA 2014 – Tool Arsenal, we demonstrated using the Tastic RFID Thief’s PCB to weaponize both an Indala – Long-Range Reader 620 and an iCLASS – R90 Long Range Reader. Illustrated in the photo below, we can see that we simply hooked up the black/red power cables and the green/white standard Wiegand DATA0/DATA1 output cables to our PCB to effectively weaponize those readers.

The folks over at ToolsWatch.org caught a good photo of the demo on their tool arsenal day 1 wrap up post – 06Aug2014.

Optimizing Read Range
Greater read distances can be achieved by reducing interference and providing clean, high voltage. For more details on improving read range, see the following resources:
- HID – MaxiProx 5375 – Product Page
- HID – MaxiProx 5375 – Installation Guide PDF
- HID – Installing the HID MaxiProx for optimum read range – AppNote 010 – (PDF)
- HID Whitepaper – Achieving Optimal Read Range – It’s all in the Frequency (PDF)
- Gorferay.com – Installing the HID MaxiProx for Optimum Read Range
Install Notes – Arduino Sketch
Note 1: The design was compiled and loaded onto the Arduino Nano v3.0 using the Arduino v1.0.1 software with the added sdfatlib (05Dec2011) library to handle the microSD card writing. See Arduino – Libraries for more info on adding additional Arduino libraries. Unzip the sdfatlib20111205.zip file and copy the “SdFat” folder to “/arduino-1.0.1/libraries/SdFat/” (starting at location where your arduino.exe program is located). If there was already an “SdFat” folder there, delete it and copy over from the zip cleanly.
Set Tools->Board value to “Arduino Nano w/ ATmega328“. Go to File->Upload to upload our sketch: Tastic_RFID_Arduino_Code.ino.
Note 2: Make sure to format the filesystem of the microSD card to FAT (not FAT32). This will require you to use a smaller size microSD card, 2GB or less. See: a cheap microSD card example product that works well here.
Note 3: Shubham Shah was kind enough to put together a blog post providing a detailed assembly guide for the Tastic RFID Thief. This guide, which is full of step-by-step instructions and photos can be found at: https://shubh.am/guide-to-building-the-tastic-rfid-thief/
Note 4: For tips on how to completely silence your HID MaxiProx 5375 reader, see our blog post: Tastic RFID Thief: Silent RFID Hacking – Bishop Fox.
LCD Faceplate - 3D printable
A 3D printable LCD 20×4 faceplate to cover the LCD rectangular hole on the front of the Tastic RFID Thief. The example below was printed using a Makerbot Replicator 2 – 3D printer.

If you are like me, you may have made a mess of cutting out the rectangle for the LCD on the plastic cover of your HID MaxiProx5375 RFID Reader.
If so, no worries. This extremely thin (0.5mm), 3D printable LCD faceplate and a little krazy glue is all you’ll need to make that LCD hole look nice and clean.

You can also find details on the 3D printable object at our Thingiverse.com page at: