
Reported Date
July 28, 2005 (disclosed at Black Hat 2005)
November 23, 2005 (sent an email to Microsoft)
Vendors
Microsoft Corporation
Guidance Software
X-Ways Software
Systems Affected
Microsoft Windows Explorer
Microsoft AntiSpyware (Beta 1)
Guidance EnCase Enterprise Edition (tested version 4 and 5)
Guidance EnCase Forensic Edition (tested version 4 and 5)
X-Ways WinHex Forensic Edition (tested version 12.65)
Summary
Windows file time stamps can be set to extremely low values via the NtSetInformationFile() system call. The Windows API does not properly translate the low 64-bit time values stored on disk into human readable format, and displays no information instead. Although this is not a security vulnerability in itself, it adversely affects third-party applications that rely upon the Windows API to perform the translation.
Vendor Status
Microsoft has been notified of the issue, but does not consider it a security issue. It has been forwarded to the products division.
Guidance Software has been aware of this issue since July 28, 2005.
X-Ways Software was never notified.
Exploit Availability
Timestomp, a Metasploit Anti-Forensics Project tool, has been made available to take advantage of this flaw. It is available for download here. (Downloads are currently unavailable.)
Researcher
Vinnie Liu
Vulnerability Details
File time stamps are stored in the FILE_BASIC_INFORMATION structure:
typedef struct FILE_BASIC_INFORMATION {
LARGE_INTEGER CreationTime;
LARGE_INTEGER LastAccessTime;
LARGE_INTEGER LastWriteTime;
LARGE_INTEGER ChangeTime;
ULONG FileAttributes;
} FILE_BASIC_INFORMATION, *PFILE_BASIC_INFORMATION;
The FILE_BASIC_INFORMATION function is used as an argument to NtSetInformationFile() to set the properties of a file. By setting very low values in a SYSTEMTIME structure and converting into a LARGE_INTEGER structure with ConvertLocalTimeToLargeInteger(), we have very low valued LARGE_INTEGER file times. Windows does not correctly translate the low valued 64-bit time stamps into the human readable format, so blanks are displayed instead.
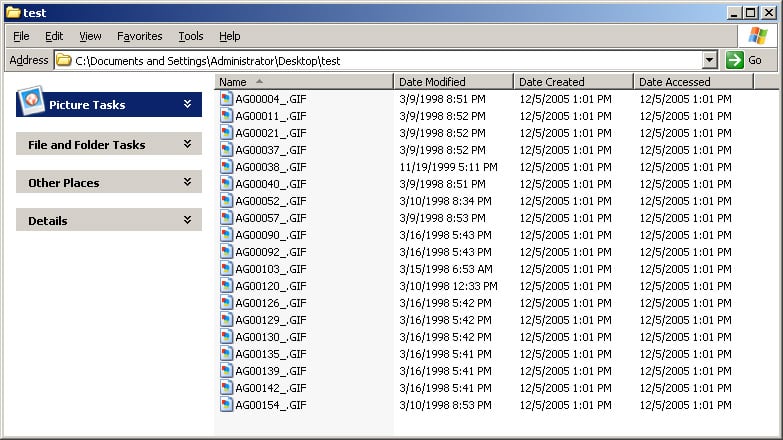
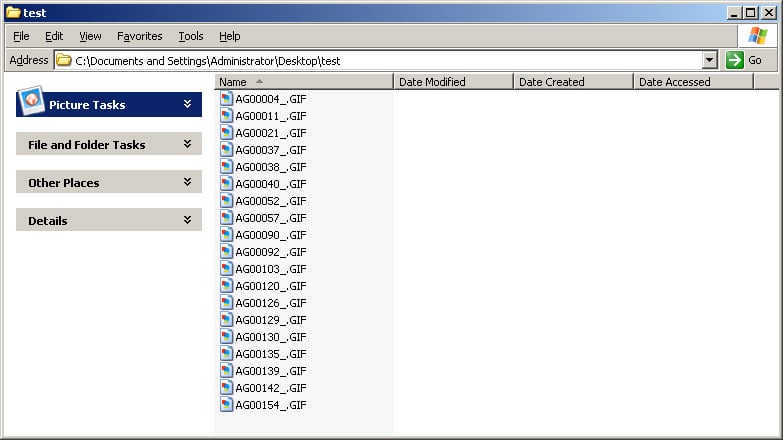
Windows Explorer
Windows Explorer relies on the Windows API function calls to translate the binary time values into human readable format. As a result, it is unable to display maliciously set file time values.
Microsoft AntiSpyware (Beta 1)
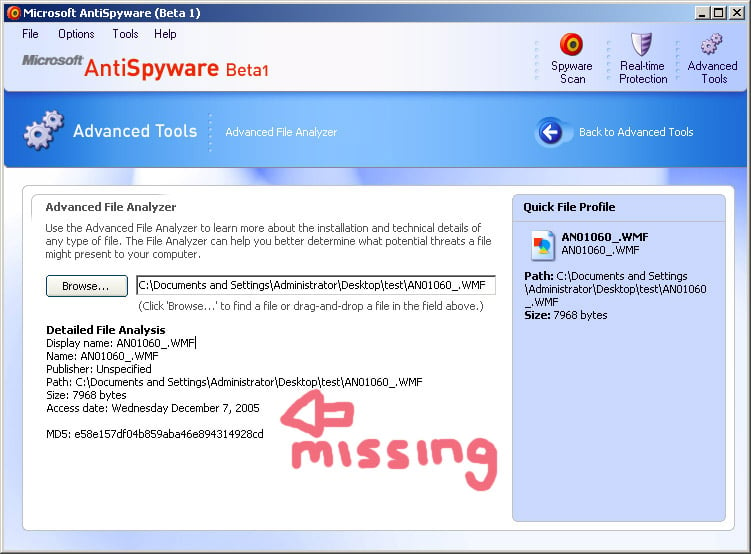
Microsoft AntiSpyware's Advanced File Analyzer feature relies on the Windows API function calls to translate the binary SYSTEMTIME values into human readable format. As a result, it is unable to display maliciously set file time values.
Guidance EnCase
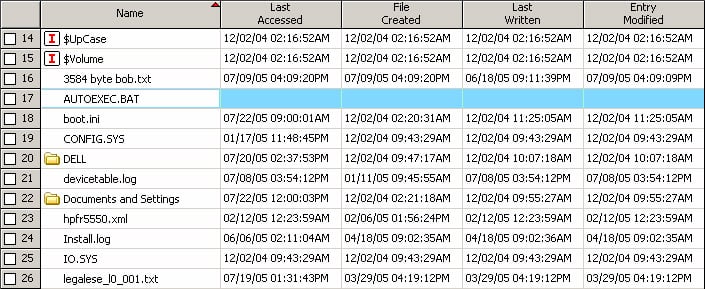
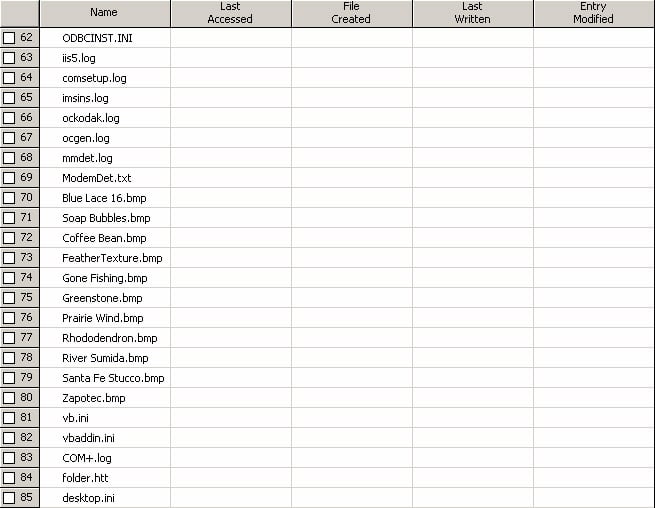
This vulnerability has the greatest impact on 3rd party forensics software that relies on the Windows API to translate the binary time stamps. Forensic examiners use time stamps both to timeline malicious activity as well as locate other potentially suspicious files. The results of these examinations is often used in court, and below we see how it is possible to invalidate time-based evidence. The first image shows the effect of Timestomp on a single file viewed through EnCase. The second image shows the effect of Timestomp against an entire volume viewed through EnCase.
Workaround
A more detailed discussion of countermeasures can be found at the Metasploit Anti-Forensics Project website.
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.


