Simple – Better Banking (Android) v. 2.45.0 – 2.45.3 - Sensitive Information Disclosure

Product Vendor
Simple Finance Technology Corp.
Product Description
Simple – Better Banking is an Android application that provides banking services for Simple.com. The project’s official website is Simple.com. The latest version of the application is 2.67.1, released on February 11, 2019.
Affected Version(s)
Versions 2.45.0 – 2.45.3
Vulnerabilities List
One vulnerability was identified within the Simple – Better Banking Android application:
- Sensitive Information Disclosure
This vulnerability is described in the following sections.
Impact
If exploited, this vulnerability could be leveraged to gain unauthorized access to user passwords. This could have adversely affected approximately more than several thousand users (as of publication, the app has been downloaded more than 100,000 times on the Google App Store.)
Sensitive Information Disclosure
The Simple – Better Banking Android application was affected by an information disclosure vulnerability that leaked the user’s password to the keyboard autocomplete functionality. Third-party Android keyboards may store this password in cleartext or transmit the password to keyboard vendors for customization purposes. A compromise of any datastore that contains keyboard autocompletion caches would result in the disclosure of the user’s password.
Vulnerability Details
CVE ID: CVE-2019-8350
Access Vector: Context Dependent
Security Risk: Medium
Vulnerability: CWE-200
CVSS Base Score: 6.6
CVSS Vector: CVSS:3.0/AV:P/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Simple’s sign-in form did not disable autocomplete for the password field, resulting in the password being stored in the keyboard’s autocomplete cache. vulnerability was self-evident during the authentication process, shown below:
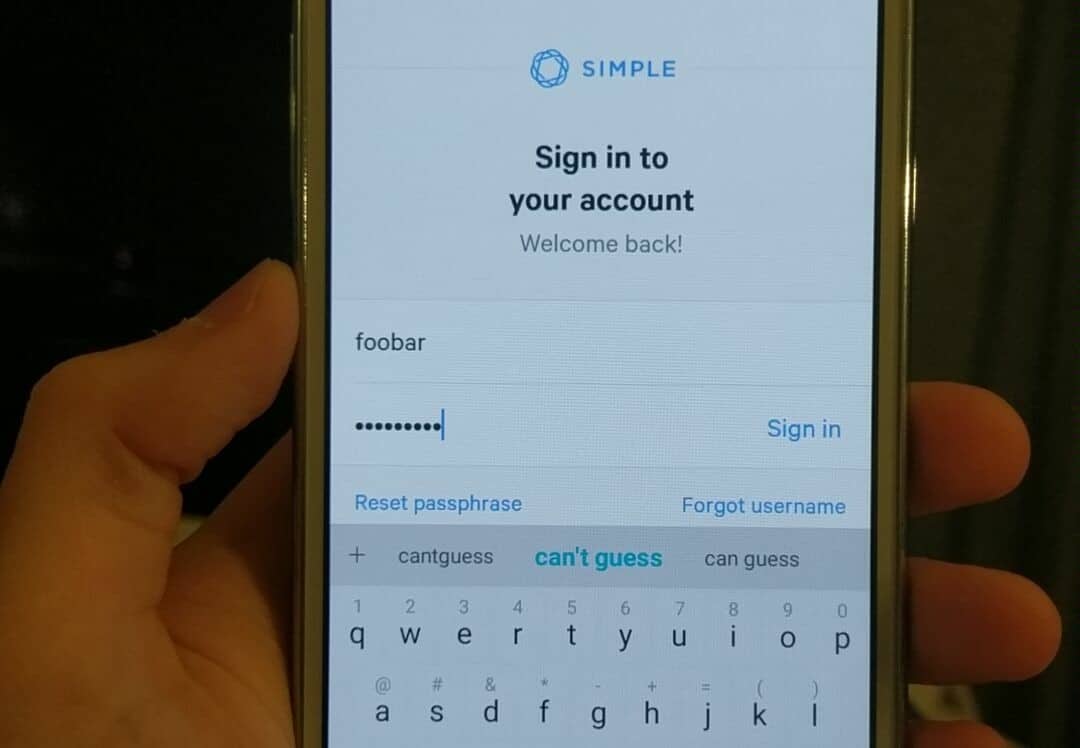
Exploitation of this vulnerability depends largely on what keyboard app was used at the time of sign-in and the functionality and security of said keyboard. On all keyboards with predictive text and dictionaries, the password will be saved to the device. Whether or not that data store is encrypted is dependent on the keyboard in use.
Another attack vector to consider is the compromise of the keyboard vendors’ cloud datastores. For example, the SwiftKey keyboard optionally provides predictive text enhancements based on the user’s dictionary and previously typed words. When enabled, the dictionary (which would include the user’s Simple password) is sent to SwiftKey servers for analysis.
Solution
Update to version 2.46.0 or later
Disclosure Timeline
- 04/23/2018: Initial discovery
- 04/23/2018: Contact with vendor
- 04/23/2018: Vendor acknowledged vulnerabilities
- 04/26/2018: Vendor released patched version 2.46.0
- 04/26/2018: Vulnerabilities publicly disclosed
Researcher
Matt Hamilton, Senior Security Analyst at Bishop Fox
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.


