
Patch Date
December 15, 2005 (pre-release version fix confirmed)
Reported Date
July 28, 2005 (disclosed at BlackHat 2005)
Vendor
PGP Corporation
Systems Affected
PGP Desktop Professional 9.0.3 Build 2932 (latest version as of release)
PGP Desktop 8.x (all versions tested were vulnerable)
Summary
PGP Desktop includes a Wipe Free Space utility that claims to eliminate data in all the free space on your hard drive including the little areas after the end of existing files which may still have old data left behind. In short, the utility claims to wipe file slack space, the unused space in a disk cluster. The software does not work as advertised. It does not clean slack space.
Vendor Status
PGP is aware of the issue, and has resolved it in their latest release.
Exploit Availability
Slacker, a Metaploit Anti-Forensics Project tool, has been made available to take highlight this flaw. (Downloads are currently unavailable.)
Researcher
Vulnerability Details
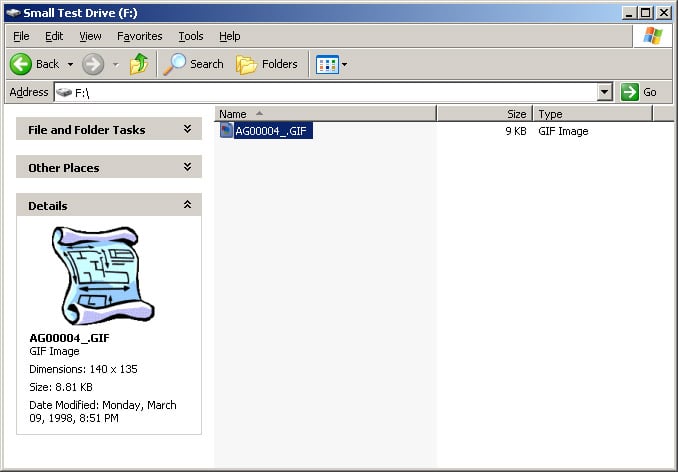
NTFS volumes allocate space for files based on fixed cluster sizes. By default, an NTFS drive will allocate 4096 bytes per cluster. Each cluster is subdivided into 512 byte sectors, by default. Because of the allocation by cluster, a file 9024 bytes in size would require more than 4096 bytes, more than 8192 bytes, but less than 12288 bytes. The file system must allocate 12288 bytes to store the file.
File slack space is the unused series of bytes from the end of a file to the end of the disk cluster. In the example above, 3264 bytes of slack space exists. In the first image below, the file, F:\AG00004_.GIF, is seen through Windows Explorer with a file size of 9k. Seen through EnCase in the second image, the file actually occupies 9024 bytes of the 12288 bytes allocated for it on disk. The series of red zeros in the lower left pane represents the file's slack space, currently empty.
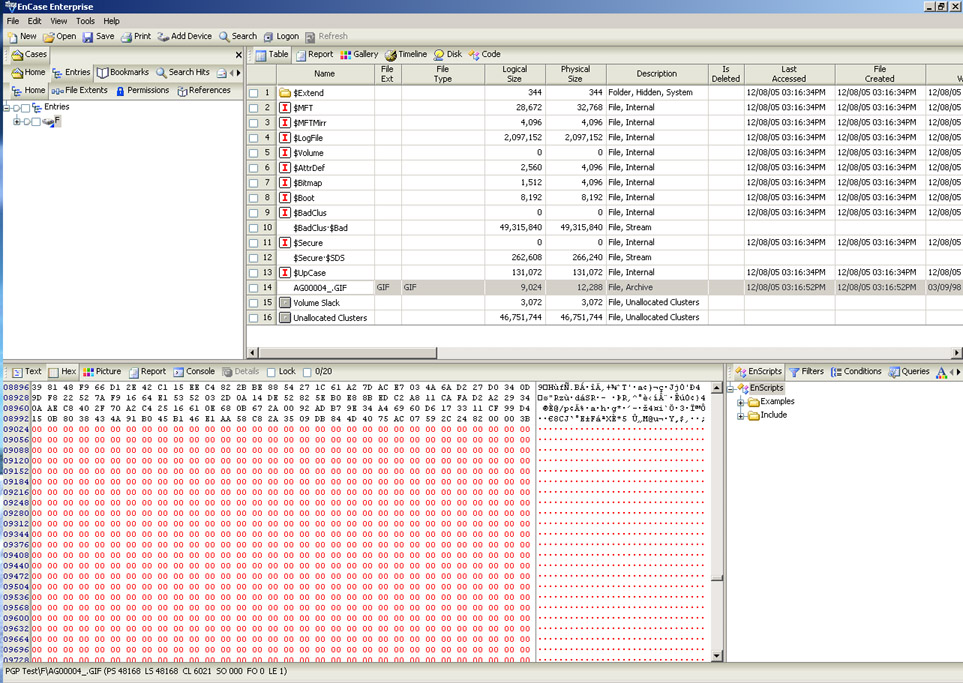
After verifying that the slack space is empty, the Slacker tool can be used to store data within the slack space of the file. Below the slack space of the file is examined with the EnCase forensic software after Slacker is used to store data in the empty space. The first image shows the start of the inserted data, and the second image shows the end of the inserted data.
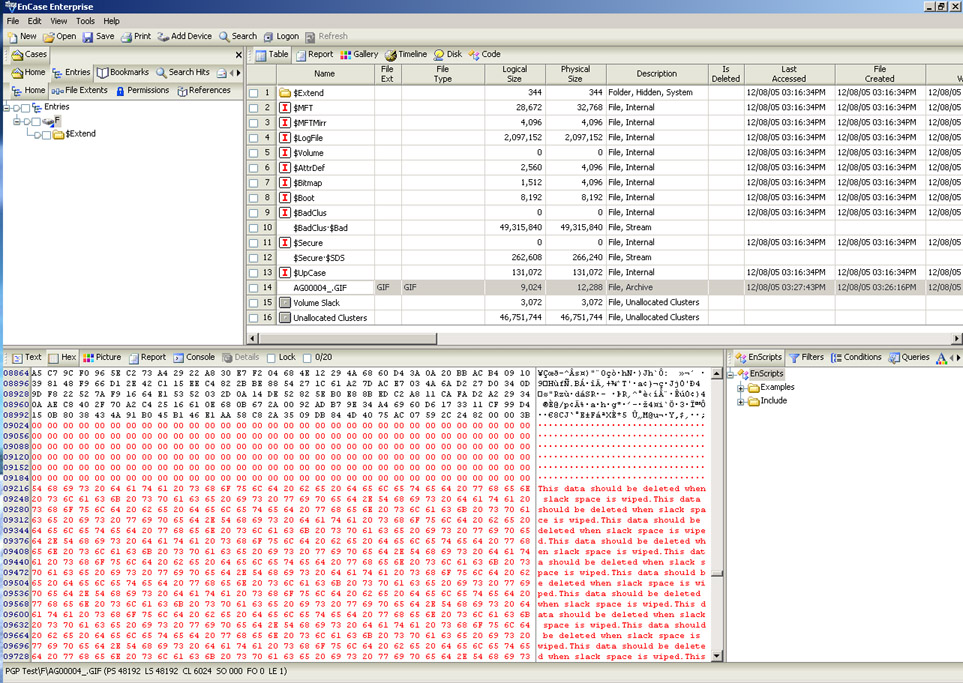
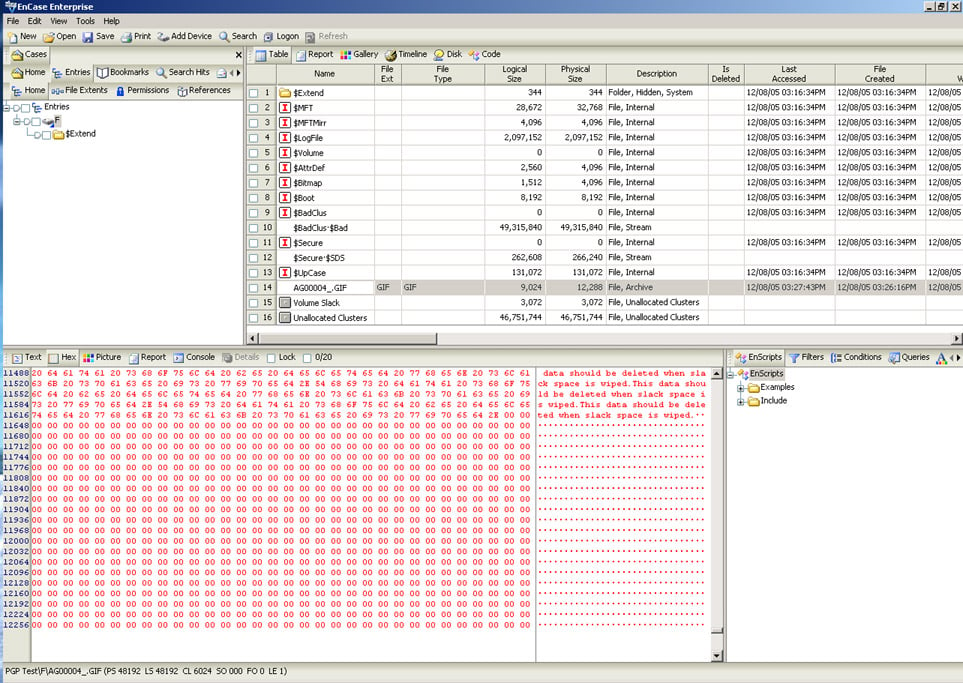
The PGP Free Space Wizard completes three passes against the entire F: volume in the image below.
According to PGP Professional, the slack space after the files should now have been cleaned of any data, but a forensic acquisition of the drive with both EnCase and WinHex after the Wipe Free Space utility has been run shows us that the data has not been changed at all.
Workaround
A more detailed discussion of countermeasures can be found at the Metasploit Anti-Forensics Project website.
Notes
August 11, 2005 - sent an email to PGP Corporation case #8857-29181922-0622
October 14, 2005 - sent an email directly to a product manager
December 09, 2005 - I would like to thank PGP for being extremely responsive, and going to great length to quickly work on the issue. We are currently working together to remediate.
December 15, 2005 - PGP Desktop Professional 9.0.4 Build 4034 confirmed to fix the issue. Thank you to PGP for the rapid turn around time and eagerness to resolve the issue for their customers.
References
- BID-15784: PGP Desktop Wipe Free Space Assistant Improper Disk Wipe Vulnerability
- CVE-2005-4151: The Wipe Free Space utility in PGP Desktop Home 8.0 and Desktop Professional 9.0.3 Build 2932 and earlier does not clear file slack space in the last cluster for the file, which allows local users to access the previous contents of the disk.
- OSVDB ID: 21569: PGP Desktop Wipe Free Space Failure
- SA17827: PGP Desktop Wipe Free Space Security Issue
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.


