Hello World! Introducing the Bishop Fox Cybersecurity Style Guide

Our newest revision, Version 1.1, is now available.
How do you pronounce SQL? Should you write denial of service with hyphens? Is it pen testing or pentesting? In the evolving world of information security, it’s hard to know who to turn to for answers to questions like these.
Through research and internal discussions over the last two years, we’ve come to a consensus about how to answer these kinds of questions for ourselves. We’ve compiled 1,775 security terms into one document that we’re calling the Cybersecurity Style Guide, and we’re very excited to share Version 1 of that guide with you today.
This style guide is not a dictionary—our goal here is to give guidance about usage, not to define the terms in detail. Each term in the guide earned its place by being unintuitive in some way:
- It may be a homonym of a non-technical word (front door, Julia, pickling),
- it may be uniquely written (BeEF, LaTeX, RESTful),
- it may not follow a clear pattern (web page vs. website),
- it may have a very specific technical distinction (invalidated vs. unvalidated),
- or its meaning may differ depending on the audience and the day (crypto, insecure, PoC).
From malicious viruses to viral memes, our guide reflects the terms that security researchers are likely to use in their technical reports, blogs, and presentations—including the contentious use of cyber- in our very own style guide title:
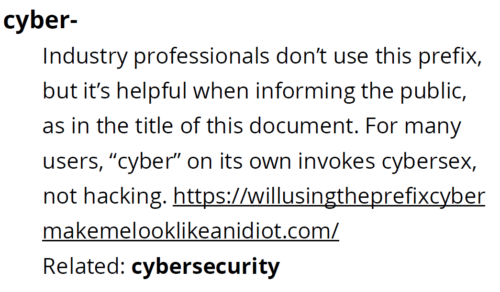
We hope that the guide is helpful to you, but this is just the beginning.
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.



