
RED TEAMING AS PART OF A HOLISTIC CYBERSECURITY PROGRAM
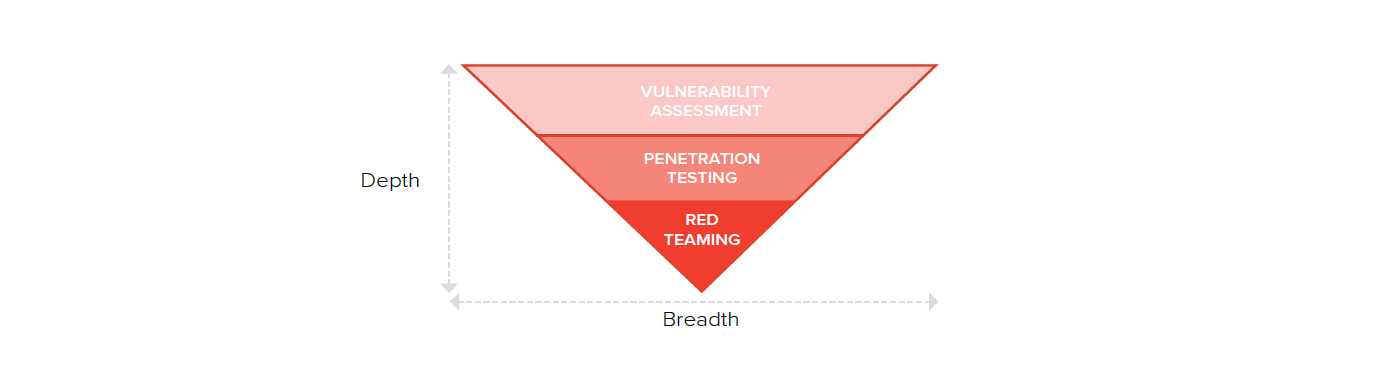
In order to fully understand red teaming, it might be best to first decouple it from penetration testing. The two are often conflated, and that only serves to lessen the quality of the decision-making around which to choose.
Red teaming exercises have a distinct value to organizations that differs from pen testing. Red teaming involves a much larger team of specialists hired from the outside — mature security programs may choose to create their own red teams — who take a mile-wide approach to infiltrating an organization. Penetration tests can have narrower focuses on specific applications or customer-facing network segments and expose vulnerabilities and weaknesses that need immediate attention and are prioritized for patching and/or updated policy-making.
Enterprises that employ red teaming as part of a regular security assessment want these crack outfits of white-hat hackers to kick down the doors any way possible. No approach is out of bounds, be it a physical infiltration coupled with a malware attack, or a simple social-engineering scheme to establish a foothold inside, red-teaming is an assault against an organization carried out much in the same way as a coordinated targeted attack.
The value of a red-teaming exercise is that it puts an organization’s detection and response capabilities and procedures to the test. It’s about much more than finding unpatched bugs and long-forgotten servers still connected to the internet. It’s about putting a company’s digital and physical security to as close to a real-world test as possible and evaluate how robust your response is.
In this guide to red teaming, we will showcase the strategy behind red teaming and its execution as part of a holistic cybersecurity program. It will also cover how tabletop exercises, threat-based assessments, and continuous testing can contribute to an organization’s strengthened security posture.
Red teaming isn’t for every organization. But mature programs do benefit from the practice — its roots are in the military and intelligence operations — as part of a continuous assessment of cyber and physical security. Threats to enterprises go well beyond cybercrime and data breaches. Some rogue nation-states are supplementing national economies with hacking, and the theft of intellectual property and penetration of critical infrastructure brings these threats closer to more and more security teams every day.
Red teaming goes beyond penetration testing of applications and network segments to one where defenses and response is tested against determined adversaries before there is real-world damage. To have a regular, carefully planned, and resourced assessment of digital and physical defenses is an imperative that few organizations in sensitive, critical industries can no longer afford to ignore.
What is a Red Team Exercise & Why Do You Need It?
Red teaming is a simulation of a cyberattack in which the red team is allowed to leverage a variety of methods in order to capture a “trophy.” This trophy is previously identified by the organization engaging in a red team exercise; it might be gaining access to a set of credentials or establishing a foothold in a sensitive internal network. With red teaming, it is not the how of getting to a destination that matters, it’s the “destination.”
Red teaming takes many forms (e.g., in the three following case studies), whether it’s a black-box engagement such as in the transit authority case study below, or a mix of external network, web application, and physical penetration testing including social engineering. Or something akin to an application penetration test combined with a network penetration test.
Red teaming is not a penetration test. A traditional penetration test is limited by the confines of scope and other pre-determined conditions. These boundaries serve their purposes in such engagements, but they can provide a narrow glimpse into your organization’s weaknesses. After all, hackers do not acknowledge such arbitrary boundaries; they don’t care if your information is hosted in the cloud, if you’re using legacy systems, or if a third-party vendor is responsible.
Red team assessments are generally longer in duration than pen testing assessments and often involve a team of several people who test several detection and response capabilities simultaneously. While you may pay attention to one particular attack vector, or focus on remediating vulnerabilities in your web applications, a red team engagement will exploit neglected security issues in your internal network or take advantage of the security challenges posed by non-technical employees.
What Does It Mean to Red Team?
The red team’s objective is to “capture” a trophy, which could be anything an organization deems of importance, be it customer personally identifiable information (PII), persistent network access, or administrator credentials.
After this trophy is determined by the targeted organization, the red team works a variety of methods to find the best suited to reach its destination. It’s a case of anything goes. It’s also important to note that organizations have the option to request the level of knowledge the red team has in the engagement. It can be a full zero-knowledge engagement, or consultants may have some level of pre-existing knowledge of network and system architecture.
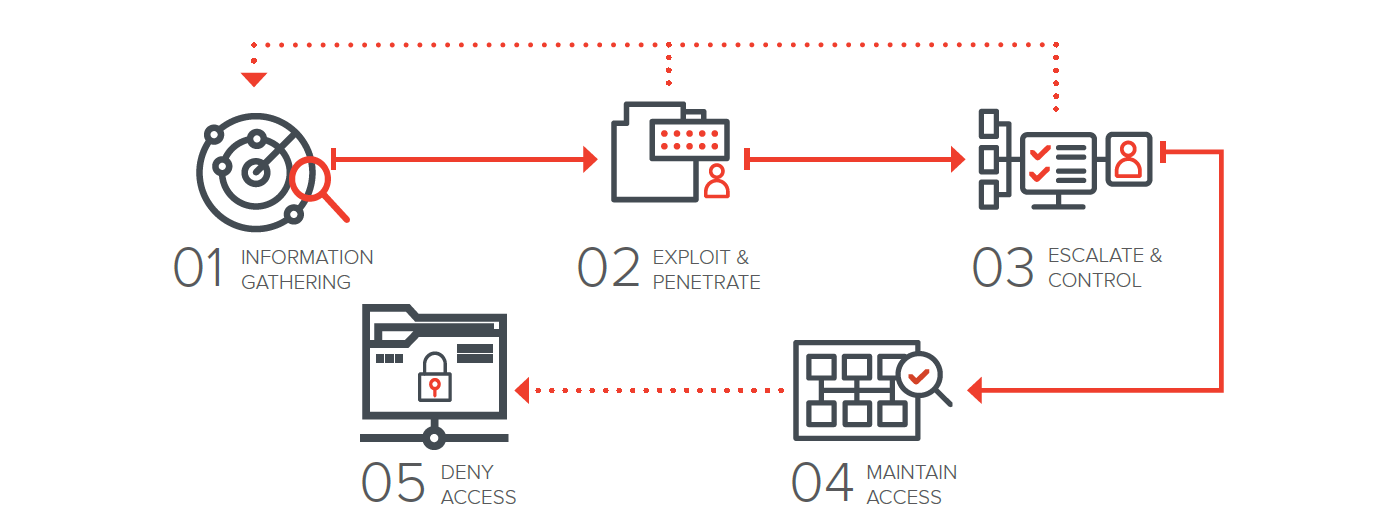
01 INFORMATION GATHERING
Gather information (footprint, domains, email addresses, etc.), analyze and determine attack methods.
02 EXPLOIT & PENETRATE
Exploit human or technical vulnerabilities and/or misconfigurations, penetrate and transmit attack via different vectors, and compromise.
03 ESCALATE & CONTROL
Install customized malware or backdoor, gain the remote control of victim’s system.
04 MAINTAIN ACCESS
Maintain the remote control and “make a persistence”.
05 DENY ACCESS
Perform the actions to achieve actual goals inside the victim’s network (persistence, lateral movement, search, exfiltration, etc.).
However, for an organization, the objective of a red team engagement will naturally differ. While the successful capture of the trophy is beneficial because it calls attention to an area of focus, your organization’s real prerogative may be to test your incident response capabilities or determine how effective your security controls are when faced with a viable threat.
Elements of a Red Team Exercise: Ways to Red Team
There are different varieties of red teaming security assessments. Below is a quick overview:
Table Top Exercises
Table top exercises involve reviewing what your most immediate and dangerous threats are — and how you would react if those threats manifested into reality. All relevant stakeholders play a part in this exercise. Perhaps you are worried about one of your employees falling victim to a phishing email and infecting your internal network with malware; perhaps you are worried about a ransomware attack wreaking havoc on your organization; or maybe you lose sleep over a denial-of-service attack bringing productivity to a halt. A table top exercise gives you the opportunity to map out all these threat models as well as how you would handle such a situation. Plan for unexpected issues when conducting a table top exercise – you may have to consider panicking executives, the fatigue of overworked employees, or possibly news breaking about the attack.
Threat-Based Simulations
To up the ante, your organization may try a threat-based simulation. At first glance, it seems an awful lot like a traditional penetration test, but there is a more to-the-point timeline involved, not all types of vulnerabilities will be assessed for, and the red team will have to do some reconnaissance beforehand. During a threat-based simulation, you focus on the threats you have previously identified — and, in a safe (but realistic) environment, you simulate them. These threats may be those that you feel you are particularly protected against or are more urgent than others.
If you think you’re ready for the challenge at hand, engage in one of these simulations. After performing a threat-based simulation, you’ll have a more pragmatic sense of your preparedness for such a situation.
Continuous Assessments
A continuous assessment is perhaps the most closely resembling a real cyberattack. This is due to the factor of time — since it’s ongoing, it represents the actual amount of effort an attacker would put in to infiltrating your organization. Several approaches will be tried to reveal where your security stance could be fortified.
Team Speak: Red Team, Blue Team, Purple Team
What is a Red Team?
A red team is meant to play the role of an attacker in a simulation. However, we’ve also mentioned the concept of a blue team. But what does a blue team do? And what’s the purpose of a purple team?
What is a Blue Team?
Think of a blue team as your first responders, like those who show up after a natural disaster in the physical world and begin the process of recovery. They are your defenders; they are those who are responsible for detecting a compromise. A red team’s success does not inherently spell failure for a blue team; rather, it’s a way for a blue team to gauge its current level of effectiveness and where they need to focus on growing and improving. In some cases, a blue team may completely miss a compromise during an engagement; use these moments as learning opportunities.
What is a Purple Team?
A purple team is a rarer component than the traditional blue or red team. It combines the capabilities of both — often segmented — groups and acts as a collaborative effort designed to implement offensive and defensive techniques. Communication is constant between those doing offensive work and those doing defensive work, whereas traditionally these two units do not interact more than necessary. You may wish to hold off conducting any sort of purple team exercise until your security team arrives at the right maturity stage.
Do you need all these teams? A red team and a blue team complement each other, so you will need something like a blue team if you do a red team engagement. A purple team, though, is reserved for more advanced security testing – and when you are at the point where both the red and blue team skill level is on par with each other.
Where to Go From Here?
Should you think red teaming might be a solution to your organization’s security woes or a proactive step to help bolster efforts before a breach or incident induces chaos, you have several options in pursuing it.
Internal Training
If you have the resources available in house to do red teaming, by all means, use them to your advantage. You may prefer to use your team for budgetary, privacy, or compliance-based reasons. If you choose to use your employees, you may want to begin with table top exercises and then ascend the red teaming hierarchy.
Work With the Right Partner
Red teaming can attract the wrong kind of security professionals. Partnering with an experienced third party vendor is another option that provides you with a true outsider view of your infrastructure — most closely resembling an attacker’s perspective. A third party will take the blinders off your security efforts and reveal weaknesses that may be missed by unintentionally biased insiders.
Are You Ready for Red Teaming?
Red teaming is more impactful when your organization is larger (typically — although not always the case), owns more assets, including the ones you may not know about, and is more advanced in terms of security. If you’re a startup that has only begun to prioritize security, then you will likely want to hold off on red teaming until you have some established defenses and a mature cybersecurity strategy implemented. You need a solid baseline in order to measure success.
If you are only starting to invest in security, you will need to take some time to conduct traditional penetration testing and understand your weak areas. Rushing into red teaming is not the best idea for a multitude of reasons — truly, you’re not at the right stage for it, and it might be overwhelming to confront all of your vulnerabilities at once.
Think of a house analogy; if you’re inspecting your house for the first time, you’re going to want to take the process in small, manageable increments. When you feel more comfortable with a sense of your perimeter, you’ll want to move on to more complicated ways someone might break in.
The Benefits of Red Teaming
Any red teaming method you choose will provide you with visibility into where your organization needs to devote more resources to improving security. Red teaming is by far the most effective and holistic method of mimicking how an attacker would likely compromise your organization. And it brings to light issues you wouldn’t have otherwise considered. By defining where you are struggling most, your organization can enhance detection and response, and decrease the risk of an attacker finding a known vulnerability already exploited in the wild.
Red teaming allows you to evaluate the value of your security controls. There is no better barometer of what works and what doesn’t work than putting your protections to the ultimate test. Also, red teaming can help you assess the capabilities of your incident response plans (aka the preparedness of your blue team). In the postmortem phases of a red teaming project, if there were breakdowns in communications or delays in detecting compromise, you will have the opportunity to improve those areas — ideally before a real incident occurs.
A successful red team assessment will also enable you to request more security budget from the C-suite for breach and attack simulation software. After determining which controls you have that are not functioning properly, where you may need to further staff your security team, and which tools you need to invest in, you can present a compelling case to allocate more budget to prioritize continuous attack emulation in your organization.
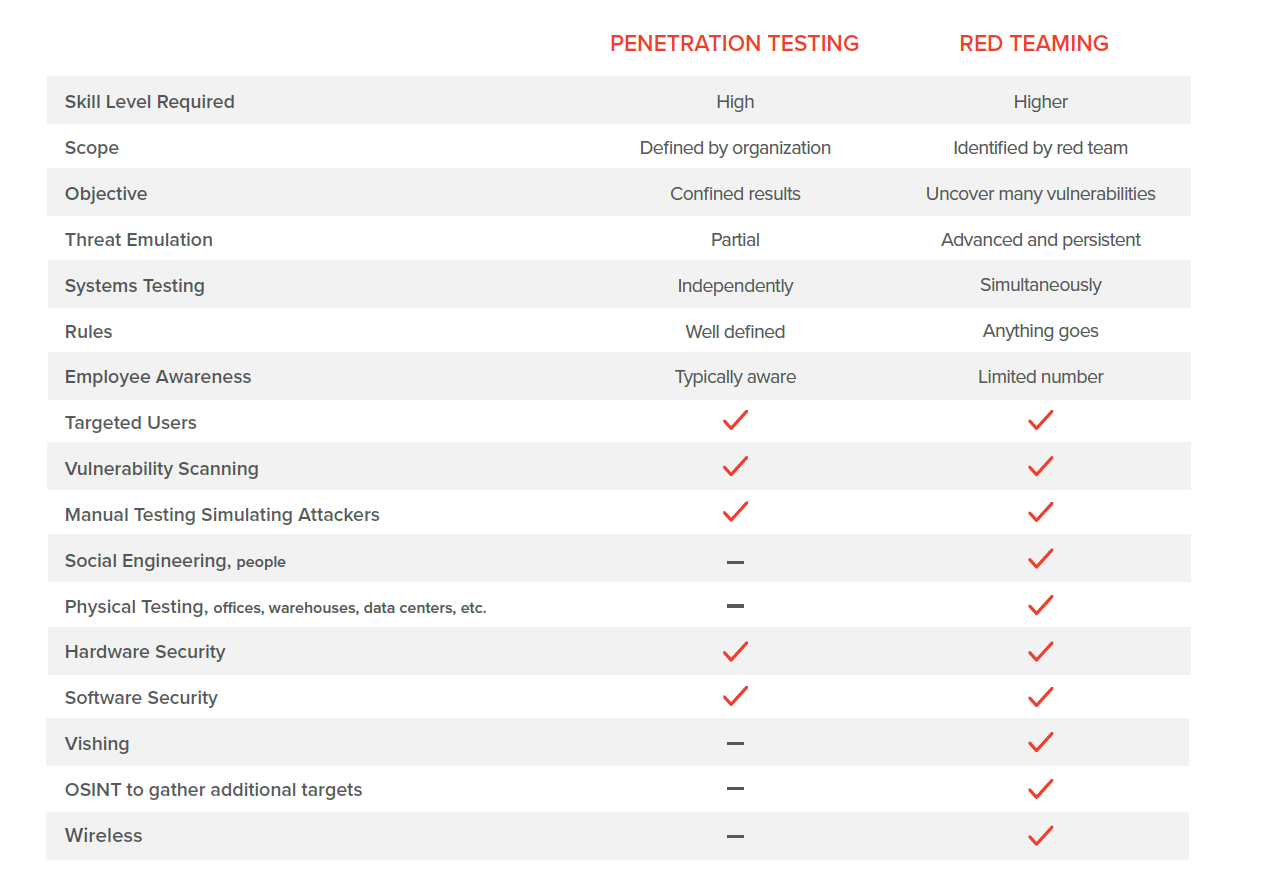
Penetration Testing vs. Red Teaming
Subscribe to our blog and advisories
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.
Recommended Posts
You might be interested in these related posts.

Apr 16, 2025
A Dark Reading Panel - "The Promise and Perils of AI: Navigating Emerging Cyber Threats"

Feb 05, 2025
From Dial Tone to Throne: IVR Testing in the Spirit of The King of NYNEX

Jan 30, 2025
Hacking the Norm: Unique Career Journeys into Cybersecurity

Jan 10, 2025
Navigating Workplace Security: Red Team Insights for the Return to Office