Hot New ‘Anonymous’ Chat App Hijacks Millions of Contact Data

By now, you may have heard the about Sarahah, the new anonymous chat application that’s gone viral around the world.
Sarahah, available for Android, iOS and via the web, allows users to send and receive anonymous messages. The app has received widespread media attention online, and now boasts a user base of between 10 and 50 million users on Android alone, according to the Google Play Store.
The app has raised concerns around cyber-bullying, but that’s only a small part of the dangers of downloading and installing Sarahah.
Both the Android and iOS applications contain functionality to send every phone number, email address, and associated names on a device to Sarahah’s servers. Exactly how this happens depends on your phone.
Upon logging into the app, Sarahah will attempt to send all phone and email contacts outbound. On iOS and Android 6+, the operating system will prompt the user before allowing access to the phone’s contacts. Phones running Android 5 and below, of which there is still a significant market share, will have no further prompt about accessing contacts beyond the Play Store permissions during installation. It’s likely that most users permit access to their contacts without considering how this data may be used.
While it’s not uncommon for mobile applications to upload your contacts as part of a ‘find your friends’ feature, Sarahah has no such functionality. The creator of Sarahah has replied that this was planned for future implementation, that no contact data is stored, and that the application will not upload contacts in the next update.
Sarahah on Android
Immediately upon logging into the Android application (or after a period of inactivity on the app), the Saharah client makes two POST requests to www.sarahah.com, which contain the Android device’s phone and email contact details (as seen below):
POST /api/account/phonecontacts HTTP/1.1 Authorization: Bearer <redacted> Content-Type: application/json; charset=UTF-8 Content-Length: 7659 Host: www.sarahah.com Connection: close User-Agent: okhttp/3.6.0
{"newContacts":[{"name":"<redacted>","phone":"+1<redacted>"},{"name":"<redacted>","phone":"+1<redacted>"},{"name":"<redacted>","phone":"+1<redacted>"}...all other phone contacts...],"oldContacts":[]}
POST /api/account/emailcontacts HTTP/1.1 Authorization: Bearer <redacted> Content-Type: application/json; charset=UTF-8 Content-Length: 547 Host: www.sarahah.com Connection: close User-Agent: okhttp/3.6.0
{"newContacts":[{"email":"<redacted>","name":"<redacted>"},{"email":"<redacted>","name":"<redacted>"},{"email":"<redacted>","name":"<redacted>"}...all other email contacts...}],"oldContacts":[]}
On Android 5 and below, these requests will be issued silently and without user interaction. With an estimated 54% of users running Android 5 and below, this is a probably a substantial amount of Sarahah’s 10 to 50 million Android users.
Android 6 introduced permissions changes, so Android 6+ will prompt the user for access to the contacts, as shown below:
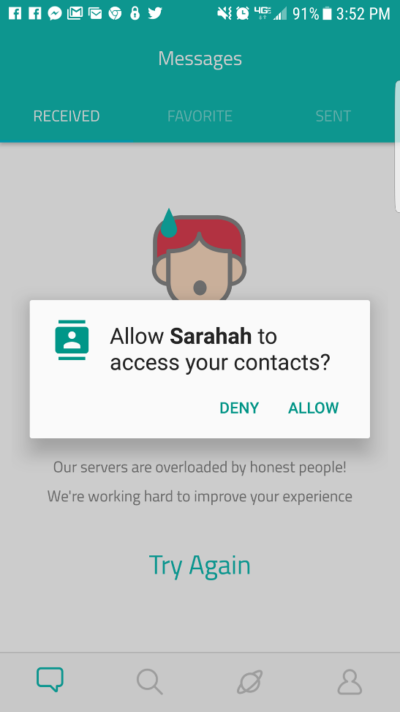
Upon pressing “Allow”, all phone and email contacts will be uploaded to Sarahah. The address book on my phone consists of 164 contacts. Extrapolating this by 10 to 50 million users on Android alone means it’s possible Sarahah has harvested hundreds of millions of names, phone numbers, and email addresses from their users. Overall, Sarahah does not provide enough information for users to make an informed decision whether using the application is worth sharing this sensitive data.
Sarahah on iOS
iOS offered more protection against this data leak, explicitly prompting whether to allow the application access to the phone’s contacts. In the prompt, the application states:
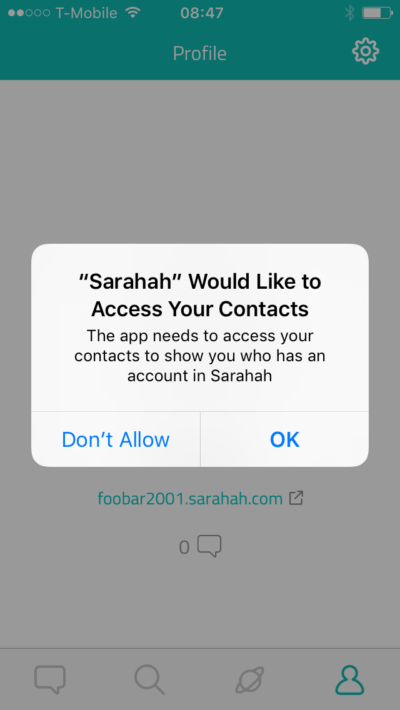
If the user presses “OK”, all phone and email contacts will be transmitted to Sarahah in the same manner as on Android. After reviewing the application on iOS and Android, I was unable to find any functionality that would require access to “contacts to show you who has an account in Sarahah.” Unfortunately, it’s probably safe to assume that the majority users on both Android and iOS simply approve access to their contacts.
How This Works
The contact-harvesting functionality can be seen in the video below. The video begins by authenticating to Sarahah on Android. After logging in and retrieving some relevant account details, the two POST requests are made, transmitting my device’s phone and email contacts respectively.
You’re Not as Anonymous As You Think.
Sarahah, on both Android and iOS, does not provide users enough information on how their phone’s contact details will be used. While this functionality is claimed to be part of a future release, and that “the database doesn’t currently hold a single contact”, unfortunately all we have is the company’s word.
With at least tens of millions of installs, consider how many phone numbers, names, and email addresses Sarahah has potentially harvested. Even names, numbers, and email addresses alone may be sensitive data for some users.
<
Subscribe to our blog and advisories
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.



