Featured Blog
Vulnerability Discovery with LLM-Powered Patch Diffing

Mar 23, 2021
If Your Scope Is Bad, Your Pen Test Will Be Bad
By Jessica La Bouve

Mar 16, 2021
How To Make Remote Work Not Suck: The Bishop Fox WFH Guide
By Britt Kemp

Mar 11, 2021
Emerging Threat Notification: F5 Networks Vulnerabilities for BIG-IP and BIG-IQ Products
By Justin Rhinehart

Mar 10, 2021
ProxyLogon (CVE-2021-26855): 2021’s Top Contender for Vulnerability for the Year (It’s March...)
By Barrett Darnell

Mar 09, 2021
Understanding the Driving Factors of a Pen Test
By Dan Petro

Mar 03, 2021
The Evolution of the Red Team
By Todd Kendall

Mar 01, 2021
CVE Digest for January and February 2021: Buffer Overflows Take the Spotlight
By Britt Kemp
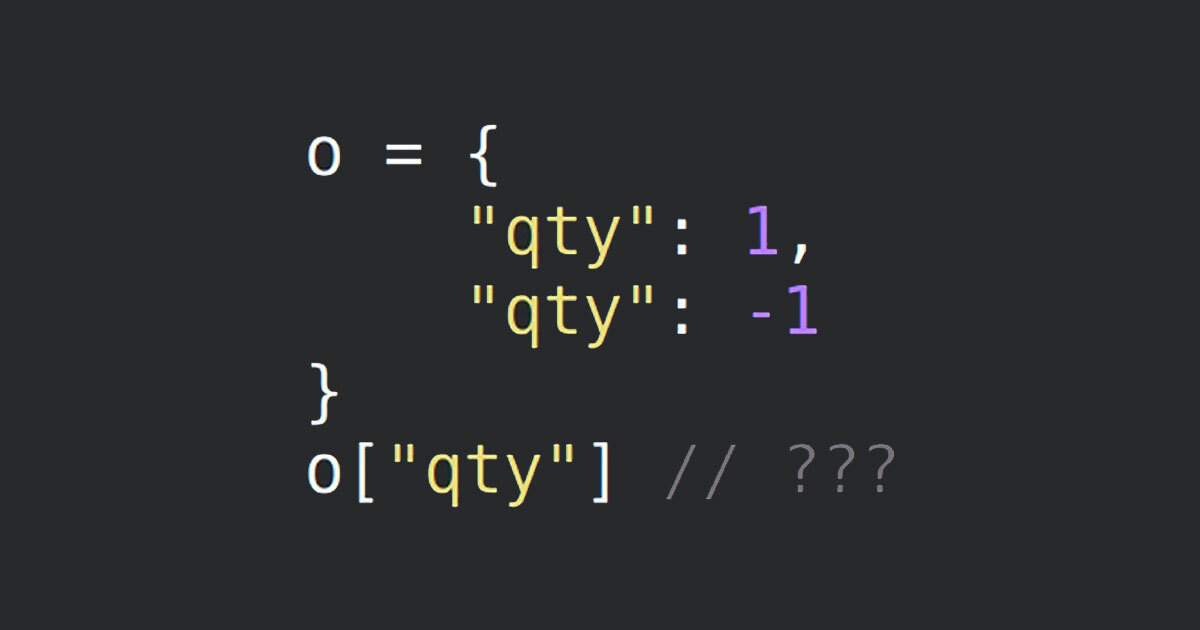
Feb 25, 2021
An Exploration of JSON Interoperability Vulnerabilities
By Jake Miller

Feb 23, 2021
What We Can Learn from the Accellion Breach
By Joe Sechman

Feb 23, 2021
Choosing the Right Modern Application Security Tools
By Tom Eston

Feb 16, 2021
When to Engage a Red Team
By Todd Kendall

Feb 09, 2021
Preparing for the Google Partner Program Security Test
By Zach Moreno
