At Bishop Fox, we regularly run product security reviews of our clients’ hardware, many of which require the use of specialized equipment. During a recent security assessment of a device that communicated exclusively over the Z-Wave protocol, we worked with Z-Wave sniffing tools and we ran into a few challenges. During the process, we learned a fair amount about Z-Wave Zniffer and Z-Wave Programmer – insights that we wanted to share with readers who may be doing similar work.
The Zniffer Basics
Z-Wave is a wireless communications protocol that uses low-energy radio waves to communicate with compliant devices. It is primarily used for home automation devices like lighting controls and smart home security systems.
To assess these types of devices, we needed to capture the communications passing through Z-Wave protocol to check both the transport-level encryption in use and the security of the Z-Wave network during the pairing and unpairing of devices. Certain downgrade attacks can be carried out during the pairing process, so to keep an eye on Z-Wave security during the event, we needed to sniff the wireless traffic to simulate what a malicious third-party attacker would do. The specific tool for sniffing Z-Wave networks is called Zniffer, created by Silicon Labs. We’re grateful they created such a useful tool for this kind of work and would like to thank them for making it available to the community.
Zniffer is an official development tool for capturing Z-Wave RF that is free after registering with the site. Since we found the flashing process tricky to get right the first time, we decided to create a detailed walk-through to help other hardware security testers get their Zniffer setup running quickly.
Hardware Equipments
Ideally, the Zniffer firmware can be flashed onto any Z-Wave compatible development stick, but we stuck to the following Z-Wave controller, which worked for our US-based testing: ACC-UZB3-U-STA
(For devices with EU-compatible RF ranges, the comparable model is ACC-UZB3-E-STA.)
We also used a Aeotec Z-stick Gen5 to build our own Z-Wave gateway. This step is optional, but it ensured that our sniffer was working as intended.
Software Requirements
To get started, download and install the official embedded development tools from the Silicon Labs menu shown below:

These tools are for the Windows platform only, and ideally, you should attempt these on a native Windows machine i.e., not a Windows VM. (Note: once the flashing process was done, we observed that the Windows VM worked just as well as native Windows for sniffing purposes.)
Steps for Flashing the Sniffer Firmware
- Unplug all other Z-Wave devices from the machine.
- Install the USB driver (not the UZB driver ) for the Z-Wave PC Programmer. It should be named
zw05xxprg.syswithin thePC\ZW050x_USB_Programming_Driverdirectory. Right click onzw05xxprg.infand hit Install. - Once you have the driver in place, plug in the Z-Wave Controller. It should be detected as a COM interface (You can double-check that within Device Manager).
- Open the Z-Wave PC Programmer. Under Settings, the Serial Interface should appear as follows:
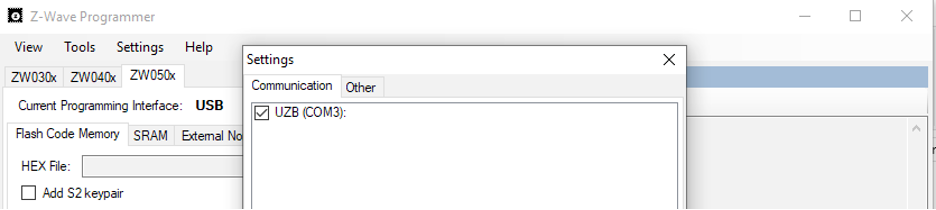
Make sure that the correct driver is loaded.
- Check for the correct driver by clicking Tools> Detect Target. If you get the following driver error, it’s most likely because the Zniffer UZB driver was installed before the USB driver.

- Install the USB driver for the Z-Wave PC Programmer and restart the application to fix this. If working correctly, the correct target should be identified as shown below:
Now that the correct target is detected, the firmware can be flashed. If the hardware is configured properly, the current Programming Interface should be set to USB by default. Under the Flash Code Memory tab, select its hex file location:Zniffer_v4_57\Z-Wave_Firmware\sniffer_ZW050x_USBVCP.hexHit Program and Verify. This process will take anywhere between 2-5 minutes and provides status updates throughout.Once the flashing process is complete, the Zniffer application can be tested.
Steps for Testing Out the Sniffer Application
- Swap the USB driver for the UZB driver. (Once the programming is done, the programmer driver is no longer needed.) Install the UZB driver from the following location:
Zniffer_v4_57\PC\uzb.inf - Unplug the Z-Wave USB device and then plug it back in.
- Restart the Zniffer application and hit Detect Modules. The correct version of the firmware should be visible within both the toolbar and the menu bars. If the firmware version was not detected (e.g., if it shows up as “COM4 (v0.00 ZW0000)”), then start over from the top—reinstall the driver, unplug/replug the device, and restart the application. There is always a possibility that the flashing process was not completed successfully.
- To make sure our Zniffer works as expected, we used the Z-Wave gateway that we set up using Aeotec Z-stick Gen5 to view the traffic:

Once we got the Zniffer up and running, we followed our product security review methodology and tested the security of the pairing process and its resilience against protocol downgrade attacks.
Official Resources for Z-Wave Developmental Tools:
Z-Wave Programmer: https://www.silabs.com/documents/public/user-guides/INS10679-Instruction-Z-Wave-Programmer-User-Guide.pdf
Z-Wave Zniffer: https://www.silabs.com/documents/public/user-guides/INS10249-Z-Wave-Zniffer-User-Guide.pdf
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.



