Arista NextGen Firewall XSS to RCE Chain

TL;DR
Arista published an advisory covering three vulnerabilities in Arista NG Firewalls. Public details initially suggested limited impact, but our researchers confirmed that the impact is far worse than originally reported, and remote code execution is possible in real-world conditions. We also found that Arista’s current patches do not fully remediate the underlying issues. Organizations should upgrade as recommended and, until comprehensive fixes are available, disable the captive portal to reduce exposure.
Summary
Last week*, Arista disclosed that its Next Generation Firewall (NGFW) appliances are affected by three high-severity vulnerabilities: sensitive information disclosure (CVE-2025-6980), authentication bypass (CVE-2025-6979), and command injection (CVE-2025-6978). The vendor released a patch (software version 17.4) to address these issues.
Bishop Fox researchers confirmed that all three vulnerabilities are exploitable. Under worst-case conditions:
- CVE-2025-6980 can expose credentials that allow VPN session hijacking.
- CVE-2025-6979 (a reflected cross-site scripting vulnerability misclassified as authentication bypass) requires victim interaction but can lead to credential theft.
- CVE-2025-6978 can be abused by an administrator for root privilege escalation or chained with CVE-2025-6979 by an attacker for remote code execution (in which case victim interaction is required).
Our researchers also found that CVE-2025-6978 was not properly mitigated and remains exploitable in the latest available software update. They identified multiple attack vectors in the vulnerable method, not all of which were addressed in the vendor's patch.
Furthermore, while researching the disclosed issues, our researchers discovered several new vulnerabilities affecting the latest available software. They are now coordinating with Arista to report and address these undisclosed vulnerabilities, for which no patch currently exists.
*Although Arista's advisory was dated October 21, Trend Micro Zero Day Initiative (ZDI) reports indicate coordinated disclosure took place on November 25.
CVE-2025-6980
The information disclosure vulnerability allows a remote, unauthenticated attacker to send an HTTP GET request to an unintentionally exposed path and receive a serialized Python dictionary in the response which contains the configuration details of one of the firewall’s installed applications:
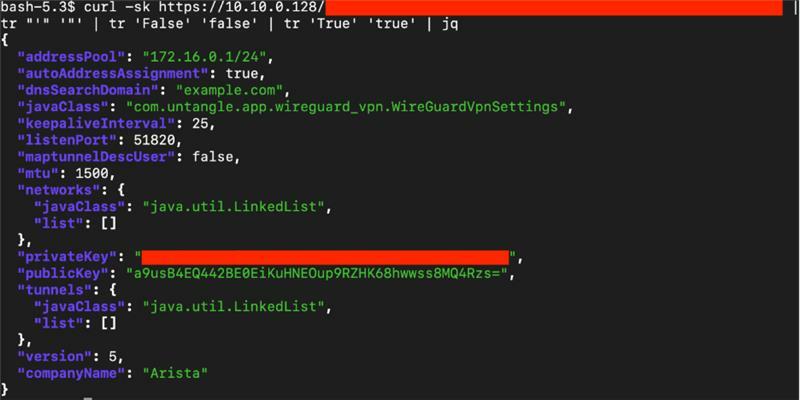
The vulnerable function can be used to reveal configuration details of selected applications running on the appliance, including:
- Captive Portal
- IPsec VPN
- OpenVPN
- Tunnel VPN (supporting multiple third-party VPN providers)
- WireGuard VPN
These configuration details may include sensitive information, like private keys and passwords, that could lead to VPN session hijacking under certain circumstances. This is likely the reason the vulnerability was assigned a CVSS base score of 7.5, despite it being more common for information disclosure vulnerabilities to fall within low- to medium-severity ranges.
The root cause of the vulnerability is apparent in the Apache configuration file capture.conf:
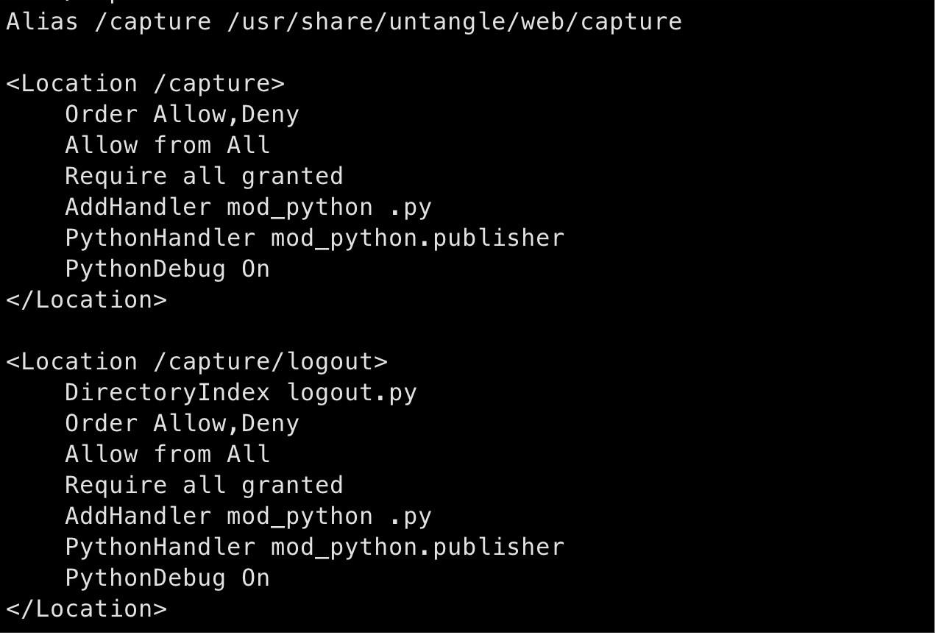
By using mod_python.publisher as a handler for the Python scripts at these two paths, the developers unintentionally exposed all functions within the scripts to public access. The patched version of the software explicitly declares which functions are intended to be internal, so publisher no longer exposes them.
Exploitation requires that the captive portal module is enabled and reachable on a public interface, even if it is not configured to capture any traffic. The vulnerability is mitigated by disabling the captive portal module or upgrading to the latest available NGFW software.
CVE-2025-6979
This vulnerability is classified as an authentication bypass in the vendor’s advisory, with no clarifying description. The ZDI disclosure contains some additional details:
This vulnerability allows remote attackers to…bypass authentication on affected installations of Arista NG Firewall. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.
This description is misleading because it initially classifies the vulnerability as an authentication bypass but then clarifies that user interaction is required. Our researchers found that it is actually a reflected cross-site scripting (XSS) vulnerability that allows arbitrary content to be injected into a page displayed by the server:
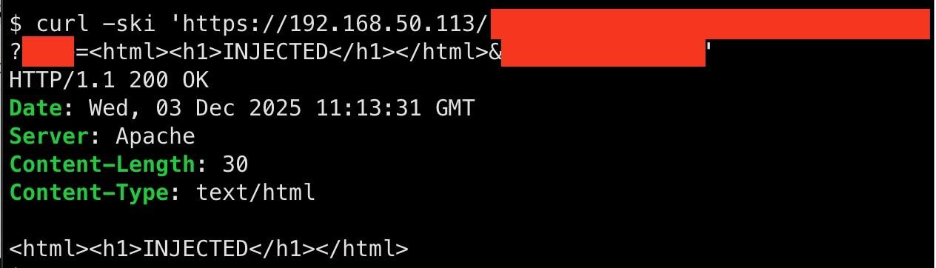
The severity of an XSS vulnerability depends entirely on its potential impact. In this case, an attacker can send a malicious URL to a firewall administrator which presents an authentic-looking login page but steals the victim’s credentials. Additionally, an attacker could craft a URL that, if the victim visits it while authenticated, can trigger a separate command injection vulnerability (see below). This is likely the reason why the vulnerability was assigned a high-severity CVSS base score of 8.8.
The root cause of this vulnerability is the same as the information disclosure described above; disabling the captive portal module or upgrading to the latest available NGFW software will mitigate it.
CVE-2025-6978
The command injection vulnerability allows a firewall administrator to inject arbitrary shell commands into a JSON-RPC request and have them executed by the server with root privilege. The NGFW management dashboard utilizes JSON-RPC requests to fulfill most administrative functions, like this (non-malicious) example:
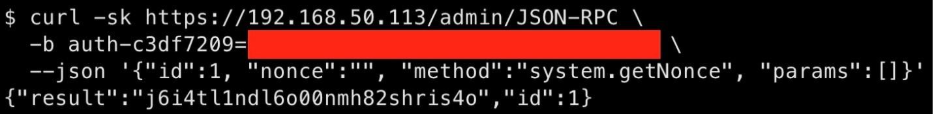
The root cause of the vulnerability is a Java handler that sanitizes user input to a particular method insufficiently. If a logged-in administrator sends a maliciously crafted request with valid session cookies, injected shell commands will be executed in the background with root privilege. An attacker can chain this exploit with the XSS vulnerability described above to trick a firewall administrator into initiating a reverse shell connection (or running any other commands they desire) without the victim’s knowledge. The right combination of victim and payload allows exploitation with a single click.
Disabling the captive portal will prevent this vulnerability from being chained with the XSS vulnerability, but it will not prevent a malicious administrator from running shell commands with root privilege. Unfortunately, our researchers found that the patch for this issue did not sufficiently mitigate it, so there is currently no way to protect against exploitation of this vulnerability by an administrator. We are coordinating with Arista to ensure a proper resolution.
Evaluating Impact
To test if your Arista firewall is vulnerable to CVE-2025-6980 and CVE-2025-6979 without causing any negative impacts, run the following cURL command:
curl -skI http[s]://[TARGET]/capture/handler.py/load_rpc_manager
A 500 Internal Server Error response indicates that the target is vulnerable, while 404 Not Found indicates the target is unaffected. Note that this command does not make any changes to the target system.
You can also download our open source Python scanner to test if you’re vulnerable: https://github.com/BishopFox/CVE-2025-6980-check
Conclusion
Bishop Fox researchers confirmed that three recent vulnerabilities affecting Arista Next Generation Firewalls are fully exploitable and, in worst-case scenarios, can lead to VPN session hijacking, credential theft, or remote code execution. Additionally, they found that the command injection vulnerability (CVE-2025-6978) was not properly mitigated and is still exploitable in the latest available software.
Be sure to upgrade your Arista firewalls immediately and/or disable the captive portal to reduce the likelihood of exploitation. Keep an eye on this blog for more information coming soon about the undisclosed vulnerabilities our researchers discovered while testing these issues.
Our Cosmos customers were notified first about our research into this vulnerability. If you’re interested in learning more about managed services delivered through our Cosmos platform, visit bishopfox.com/services/cosmos.
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.
Recommended Posts
You might be interested in these related posts.

Apr 19, 2024
PAN-OS CVE-2024-3400: Patch Your Palo Alto Firewalls

Mar 01, 2024
CVE-2024-21762 Vulnerability Scanner for FortiGate Firewalls

Sep 10, 2025
Fireside Chat - SaaS Security: Inside Recent Attacks Disrupting Global Enterprises

Mar 03, 2026
Beyond Electron: Attacking Alternative Desktop Application Frameworks


