
LastPass Site Password-Stealing Clickjacking Vulnerability
Release Date
July 1, 2015
Patch Date
April 22, 2015 - Patch issued for Chrome
Reported Date
April 3, 2015
Vendor
LastPass
Systems Affected
LastPass browser extension <3.9.2 for all browsers. Exploit is browser agnostic.
Summary
LastPass, a popular password management service with extensions for Firefox, Chrome, and Internet Explorer, suffers from a clickjacking vulnerability. It can be exploited on sites without proper X-Frame-Options headers to steal passwords. The password autofill dialogue can be overlaid with a deceptive webpage that tricks users into copying and then pasting passwords into an attacker’s site.
Vendor Status
LastPass was alerted about this vulnerability via their security issue reporting system on April 3, 2015. The LastPass team confirmed the issue on April 4, 2015 and a patch for the Chrome web browser was released on April 22, 2015. A patch for Internet Explorer soon followed.
Exploit Availability
This exploit works by clickjacking a target website; it overlays a deceptive DOM element to hide the framed site from view. The victim is then presented with various prompts designed to trick him into copying the LastPass saved password for the target site. An example of this deceptive layout can be seen below:
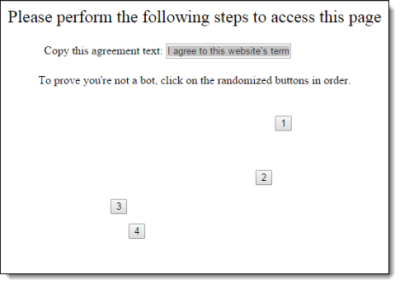
When the deceptive DOM overlay is made slightly transparent, it is revealed that the user is actually using the LastPass saved password menu, as seen here:
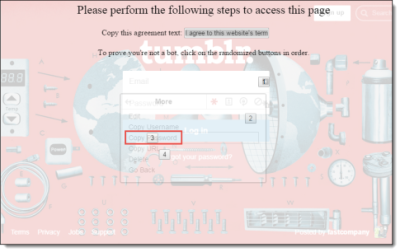
By clicking through these dialogue options, the victim is unknowingly selecting and copying the site's password to his clipboard. The victim is then finally prompted to paste the "Agreement Text" back into a text box — unaware that he’s just copied the target site's password:
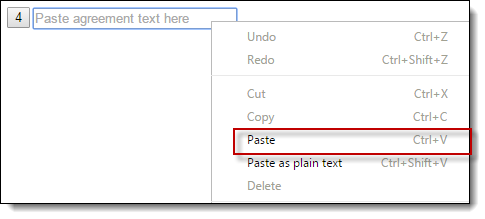
The password is then stolen via JavaScript:
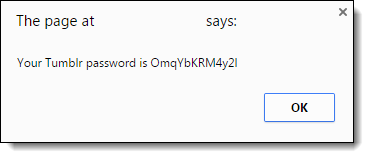
Researcher
Matt Bryant of Bishop Fox
Vulnerability Details
This vulnerability potentially allows for the disclosure of LastPass saved passwords for services such as bank accounts, email accounts, and other accounts that contain sensitive information. Due to LastPass’s quick response, all current versions are safe from this attack. To patch against this vulnerability, please update your LastPass add-on/extension to the latest version.
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.






