Invasion of the Face Changers: Halloween Hijinks with Bluetooth LED Masks

Halloween is one of my favorite holidays of the year because it means autumn is in full swing, candy corn is in season, and it’s the one night where it’s socially acceptable to go outside wearing a cloak. My family also loves Halloween, so we tend to match our costumes up with themes. We decided that this year’s theme would be “anything that glows,” and so like any responsible nerd, I dove into the world of LED contraptions to use as a centerpiece. I find that LED masks are a popular option and have all sorts of neat features and functionality that I can use for a costume, ensuring that I outshine everyone else, both figuratively and literally. I purchased a Bluetooth Low Energy (BLE)-enabled mask with custom faces controlled from an app, as I think a Shy Guy-esqe blank face is the perfect blend of interesting and unsettling to unexpectedly find in your neighborhood. One order later, I get to work with putting everything together in preparation for Halloween night.

Initial Impressions

In fact, it was shockingly easy, and in my line of work “shockingly easy” is usually a descriptor applied right before things go horribly wrong (or right, depending on your point of view). I found the app automatically scanned for, found, and then controlled my brand new, out-of-the-box mask without so much as a single authentication check, giving me some insight into how these masks worked. I’m no stranger to reverse engineering IoT devices or other smart things, and one of the first things we check for is if (and how) devices use secure communications when connecting over classic Bluetooth or BLE. It was fairly clear that there was no pairing or authentication checks happening, and so, in theory, any mask could be controlled via another BLE device, with or without the mask owner’s permission.
On its own, this information wasn’t particularly interesting, as it just means that one type of mask from one company has one security flaw… except that this wasn’t quite true. As it happens, the mask I obtained was a great example of the practice of white-labeling, which is a common practice for IoT devices and other electronics. Essentially, it means that a product is designed and built by one company, then sold to multiple other companies who resell it under their own brand. As it happens, even though online stores offered multiple brands of LED masks, essentially every single one was the same product, which is commonly called the Shining LED Mask.
Suddenly, instead of this issue affecting one specific mask, it appeared to affect many BLE-enabled mask of this type, which is quite popular and widely used especially on a night like Halloween. Armed with this knowledge, I explored the full extent to which this might be exploitable, as I always love running down a good and technically interesting prank.
Projecting An Aura of Hacks
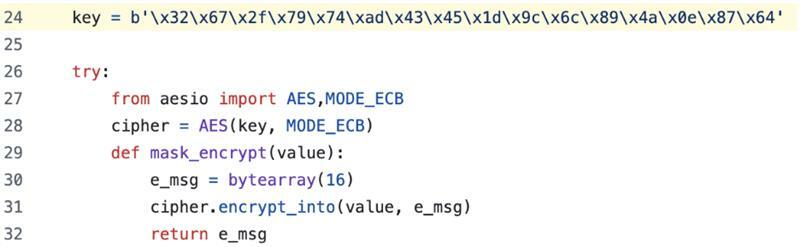
Luckily there’s already been a fair bit of work done on reverse engineering the BLE protocol used by these masks. Based on available research, there are some protections that appear to be applied between the Shining Mask and its associated app. However, these protections are AES encryption of Bluetooth messages with a known key that can be retrieved by simply decompiling the app. A tool like JADX is my normal go-to for this type or work, but it turns out we can just get the key from GitHub.
This knowledge, combined with code from other hackers and a night or two spent combing through Bluetooth snoop logs gave me enough information about the protocol to be able to build my own mask controller. This means that I can automatically change the face of any mask around me (except mine, of course) without needing to look down at my phone or fiddle with any buttons, perfect for a night out trick-or-treating.
Using an Adafruit BLE Feather board and the same previous work as a baseline, I put together a CircuitPython script to search for local Shining Masks, connect, upload a new image of a fox, and then change the face to the new image before disconnecting. You can find the full code and instructions in the Bishop Fox GitHub repository.
Figure 5: Changing everyone else’s faces, hands free with my own controller
Range is limited to “BLE local,” so you won’t be changing faces across the globe, but you can comfortably put this in your pocket and walk down the street on Halloween night, automatically changing the face of every person you see with the same LED mask.
So, what’s the fix?
The short answer is “add a pairing workflow, so only approved devices can control each mask.” But the reality is a bit more complicated.
These masks have been available for years (as evidenced by all the previous research, which is at least four years old at the time of writing this blog) and obviously working great already. Therefore, there’s not much incentive for the manufacturer to update the BLE control protocol since that would require firmware updates across every single device.
Given the difficulty of deploying this type of fix and the practical range of BLE connections, the real impact here is likely limited to “anyone within a short (10m or less) range can change your mask to any image they want,” which falls somewhere between “harmless prank” and “mild annoyance.” Even if fully exploited, the action to correct these “hacked” masks is to simply change it back to the desired image and probably have a good laugh. To err on the side of caution, we’ve hard-coded the image in our exploit code, just to help keep things family friendly for everyone.
In any case, have a safe (and as much as you can, secure) Halloween night!
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.



