
The following document describes identified vulnerabilities in the Arista NG Firewall product, version 17.4.
Product Vendor
Arista Networks
Product Description
Arista NG Firewall is a network security platform that provides firewalling, VPN, reporting, web filtering, and captive portal services through a centralized web UI. The product's official website is https://www.arista.com/en/solutions/security/etm. The latest available version is 17.4.1, released on February 3, 2026.
Vulnerabilities List
Six vulnerabilities were identified affecting the Arista NG Firewall product:
- Arbitrary Command Injection in the diagnostics feature (CVE-2025-6978)
- Arbitrary Command Injection in a password encryption helper (CVE-2026-25620)
- Insecure Input Validation in the Reports application (CVE-2026-25621)
- Arbitrary Command Injection in the Captive Portal custom handler (CVE-2026-25622)
- Overly permissive RPC interface (CVE-2026-25623)
- Reflected XSS (CVE-2026-25624)
Affected Version
17.4
Summary of Findings
Bishop Fox staff identified six vulnerabilities in Arista NG Firewall version 17.4. The most severe issues allowed Bishop Fox staff to execute arbitrary commands as the root user on the appliance. Additionally, Bishop Fox staff found that by chaining several of the vulnerabilities, they could execute arbitrary code on an Arista NG Firewall appliance by convincing a logged-in administrator to browse to a malicious URL. One of the identified vulnerabilities could also be exploited by an attacker without credentials under specific circumstances.
Arista Networks released a security advisory for these vulnerabilities on 02/03/2025.
Solution
Update to version 17.4.1.
Timeline
- 12/03/2025: Initial vulnerabilities discovery
- 12/11/2025: Vulnerability report completed and submitted to Arista PSIRT
- 12/11/2025: Arista PSIRT acknowledged reception of the report
- 02/03/2026: Arista Security Advisory 0133 published, version 17.4.1 released
Arista NG Firewall Version 17.4 Vulnerabilities
CVE-2025-6978 - Arbitrary Command Injection in the Diagnostics Feature
During their previous investigations into Arista NG Firewall vulnerabilities, Bishop Fox staff found that the previous patch for CVE-2025-6978 was incomplete and only verified input fields that could be modified by the end user through the administration web interface. This meant that other arguments sent to the diagnostics script could be manipulated to inject arbitrary commands to be executed on the remote system.
Vulnerability Details
CVE ID: CVE-2025-6978
Vulnerability Type: OS Command Injection
Access Vector: Remote
Impact: Code execution
Security Risk: High
Vulnerability: CWE-78
The root cause of the vulnerability is a Java handler that sanitizes
user input to a particular method insufficiently. If a logged-in
administrator sends a maliciously crafted request with valid session
cookies, injected shell commands will be executed in the background with
root privilege. An attacker can chain this exploit with the XSS
vulnerability described below (CVE-2026-25624) to trick a firewall administrator into
initiating a reverse shell connection (or running any other commands
they desire) without the victim’s knowledge. The right combination of
victim and payload allows exploitation with a single click.
The 17.4.1 release now includes proper validations of all input parameters that are received by the runTroubleshooting method to ensure that each parameter matches their expected format.
CVE-2026-25620 - Arbitrary Command Injection in a Password Encryption Helper
Bishop Fox staff determined that a shared password encryption helper in the Arista NG Firewall code base constructed a shell command using unsanitized user input. The helper method was used by multiple features (e.g., Active Directory configuration, PPPoE settings, Tunnel VPN settings, and Captive Portal Local Directory authentication), making it a repeated injection point. In most cases, the attacker needed admin access to trigger the vulnerability, but the Captive Portal login form could expose the issue under specific configurations.
Vulnerability Details
CVE ID: CVE-2026-25620
Vulnerability Type: OS Command Injection
Access Vector: Remote
Impact: Code execution
Security Risk:Medium
Vulnerability: CWE-78
The root cause of this issue was in the PasswordUtil.getEncryptPassword method, which contained the following code:
public class PasswordUtil
{
private final static String passwordEncryptionCmd = "/usr/bin/password-manager -e ";
// ... omitted for brevity...
public static String getEncryptPassword(String password){
try {
if (password == null) {
throw new IllegalArgumentException("password can not be null.");
}
if(password.isEmpty() || password.isBlank()){
password = Constants.EMPTY_STRING;
}
String command = passwordEncryptionCmd + password;
return execCmd(command);
} catch (IllegalArgumentException | IllegalStateException e) {
logger.error("Password can not be null or encryption output is invalid.", e);
}
catch (Exception e) {
logger.error("Exception occured while encrypting the password", e);
}
return null;
}
// ... omitted for brevity...
public static String execCmd(String command){
String cmdOutput = UvmContextFactory.context().execManager().execOutput(false, command);
String[] encryptOrDecryptPassword = cmdOutput.split(Constants.NEW_LINE);
if (encryptOrDecryptPassword.length <= 1) {
throw new IllegalStateException("Output is invalid.");
}
return encryptOrDecryptPassword[1];
}
// ... omitted for brevity...
}As shown above, the getEncryptPassword method constructed a shell command to be executed by the execCmd method by concatenating the supplied password to a string containing the base command. This meant that any user-provided password that was passed to the getEncryptPassword method could be used to inject arbitrary commands, resulting in root-level command execution on the appliance.
Bishop Fox staff found that almost all password fields used in the configuration interface to set up secrets or private keys were valid injection points. These would require an attacker to be logged in as an administrator to the appliance to be exploited.
However, Bishop Fox staff also found that under specific conditions, the password field from the Captive Portal authentication page was vulnerable to the same issue, which means an unauthenticated attacker could trigger this vulnerability. The Captive Portal would need to be configured with basic authentication, and use the Local Directory authentication backend for the Captive Portal application to be vulnerable. Moreover, the attacker would need to know a valid username from the Local Directory backend to successfully exploit this vulnerability.
The 17.4.1 release now uses a Java ProcessBuilder and tokenized input to prevent arbitrary command injection in the getEncryptPassword method.
CVE-2026-25621 - Insecure Input Validation in the Reports Application
The Reports application has a backup and restore feature that accepts GZIP compressed SQL files. The restore pipeline passes the uploaded content to the psql binary without validation, allowing crafted SQL payloads to invoke OS commands via PostgreSQL features such as COPY ... TO PROGRAM. Successful exploitation yields OS-level access as the postgres user and full database control.
Vulnerability Details
CVE ID: CVE-2026-25621
Vulnerability Type: Insecure Input Validation
Access Vector: Remote
Impact: Code execution
Security Risk: Medium
Vulnerability: CWE-78
Bishop Fox staff found that the restore feature from the Reports application would eventually pass the uploaded backup file to a shell script located at /usr/share/untangle/bin/reports-restore-backup.sh, without any kind of prior validation:
#!/bin/bash
function doHelp() {
echo "$0 [options]"
echo "required options: "
echo " -f input_file (file to write)"
echo "optional options: "
echo " -h (help)"
echo
}
while getopts "f:h" opt; do
case $opt in
h) doHelp;exit 0;;
f) FILE=$OPTARG;;
esac
done
if [ -z "$FILE" ] ; then
doHelp;
exit 1;
fi
zcat $FILE | psql -U postgres uvm 2>&1 | grep -v 'already exists'An authenticated attacker could craft a malicious backup file and use the Import / Restore Data Backup Files file upload form to trigger remote code execution as the postgres user.
The 17.4.1 release now contains extensive validation of the backup file in an attempt to prevent arbitrary code execution or arbitrary SQL instruction from being executed on the remote server.
CVE-2026-25622 - Arbitrary Command Injection in the Captive Portal Custom Handler
The Captive Portal application had (at some point) support for customized landing pages. Although this feature does not seem to be available through the web interface anymore, the API handler was still present in the code base in version 17.4 and was vulnerable to arbitrary command injection.
Vulnerability Details
CVE ID: CVE-2026-25622
Vulnerability Type: Insecure Input Validation
Access Vector: Remote
Impact: Code execution
Security Risk: Medium
Vulnerability: CWE-78
The Captive Portal custom upload handler constructed shell commands by concatenating a user-controlled argument into the command line:
@Override
public ExecManagerResult handleFile(FileItem fileItem, String argument) throws Exception
{
// ...omitted for brevity...
String customPath = (System.getProperty("uvm.web.dir") + "/capture/custom_" + argument);
// ...omitted for brevity...
try {
int checker = 0;
zipFile = new ZipFile(tempFile);
Enumeration<? extends ZipEntry> zipList = zipFile.entries();
while (zipList.hasMoreElements()) {
ZipEntry zipEntry = (ZipEntry) zipList.nextElement();
String fileName = zipEntry.getName();
logger.debug("Custom zip contents: " + fileName);
if (fileName.equals("custom.html") == true) checker += 1;
if (fileName.equals("custom.py") == true) checker += 1;
}
if (checker == 0) {
tempFile.delete();
return new ExecManagerResult(1, "The uploaded ZIP file does not contain custom.html or custom.py in the base/parent directory");
}
} catch(ZipException zip)
{
// ...omitted for brevity...
}
UvmContextFactory.context().execManager().execSafe(CAPTURE_CUSTOM_REMOVE_SCRIPT + " " + customPath);
UvmContextFactory.context().execManager().execSafe(CAPTURE_CUSTOM_CREATE_SCRIPT + " " + customPath);
UvmContextFactory.context().execManager().execSafe("unzip -o " + CAPTURE_TEMPORARY_UPLOAD + " -d " + customPath);
tempFile.delete();
logger.debug("Custom zip uploaded to: " + customPath);
return new ExecManagerResult(0, fileItem.getName());
}The argument value becomes part of a path used in
three separate command executions, enabling command injection.
Exploitation requires an authenticated administrator and a ZIP archive
containing a custom.html or custom.py file to reach the vulnerable
path.
The 17.4.1 release completely removes this feature from the code, neutralizing the vulnerability.
CVE-2026-25623 - Overly Permissive RPC Interface
Arista NG Firewall extensively relies on a JSON-RPC mechanism as its main API component. Bishop Fox staff found that the admin RPC endpoint exposed an overly permissive interface which could be used to access other dangerous interfaces such as theExecManager interface. Authenticated administrators could access these dangerous interfaces to execute arbitrary commands as the root user on the appliance.
Vulnerability Details
CVE ID: CVE-2026-25622
Vulnerability Type: Insecure Input Validation
Access Vector: Remote
Impact: Code execution
Security Risk: Medium
Vulnerability: CWE-78
The JSON-RPC endpoint exposed the UvmContext interface, which provides access to high-privilege managers such as ExecManager and ConfigManager. Such interfaces could be accessed via the rpc object in JavaScript, and used to execute arbitrary commands on the remote system:
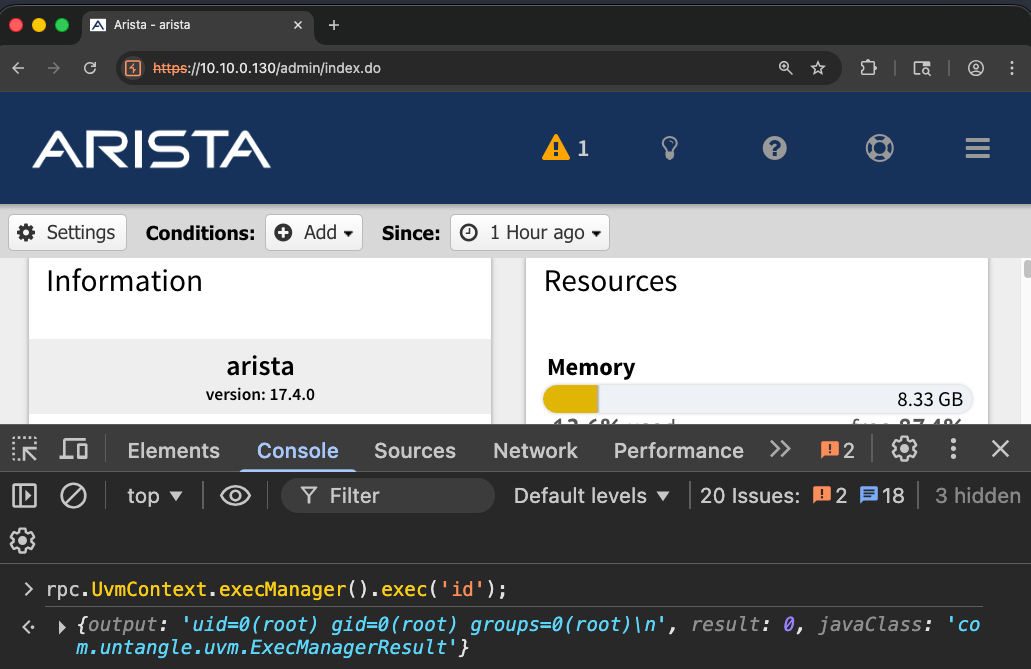
An attacker with administrative access to the appliance could execute arbitrary commands as the root user.
The 17.4.1 release new uses a new class called SafeUvmContext that is a sanitized version of the UvmContext interface, and does not expose the ExecManager interface anymore.
CVE-2026-25624 - Reflected XSS
Bishop Fox staff found two instances of reflected Cross-Site Scripting on the /quarantine endpoint that could be used in an exploit chain in combination with CVE-2026-25623 for a 1-click RCE on Arista NG Firewall appliances.
Vulnerability Details
CVE ID: CVE-2026-25622
Vulnerability Type: Insecure Input Validation
Access Vector: Remote
Impact: Escalation of privileges
Security Risk: Low
Vulnerability: CWE-79
Two JSP templates under the /quarantine endpoint lacked the JSTL core taglib declaration. As a result, a debug parameter value was reflected into the response without proper handling, enabling reflected XSS. This issue was used to trigger JSON-RPC calls in a logged-in administrator’s browser and chain to command execution.
The 17.4.1 release now includes the missing taglib instruction, which properly fixes this vulnerability.
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.






