Most Security Programs Test a Fraction of Their Applications. That Changes Today.

This week, Bishop Fox announced the evolution of its application penetration testing services, powered by Cosmos AI. Before I walk through what this means for your program, I want to start with a question every application security leader eventually faces:
What metrics do you report to your board, your CISO, or your VP of Engineering to prove your AppSec testing program is working?
The answer to that question matters more than any technology announcement. Because the real measure of AI in application security is not how many vulnerabilities an AI agent can find but whether AI moves the needle on the outcomes your program is accountable for delivering.
Every organization we work with is on a maturity journey. Some are trying to pass their next audit, while others are trying to prove security ROI to the board. But we find most are somewhere in between, trying to test more applications, reduce remediation timelines, or integrate security into their release pipeline without slowing down engineering.
Cosmos AI is built to accelerate that journey, wherever you are on it.
The Coverage Problem No One Talks About
Here’s the reality most application security leaders live with: the majority of your application portfolio has never been tested by an expert.
Not because you do not care, but the math simply does not work.
Traditional penetration testing requires scoping calls, questionnaires, SOW negotiations, weeks of scheduling, and dedicated consultant time for every engagement. Multiply that by the number of applications in your portfolio, and you quickly understand why even well-funded programs only test a fraction of what they own.
The result is a coverage gap that grows every time engineering ships a new application or microservice. Security teams end up making impossible choices about which applications deserve expert attention, while the rest carry unknown risk.
This is not a tooling problem though; it is operational. And that is exactly what Cosmos AI changes.
Submit a URL. Get Validated Findings.
With Cosmos AI, requesting an application penetration test works like this: submit a URL. That is it.
No mandatory scoping exercise. No weeks of pre-engagement coordination. No SOW negotiation for every application. You can spend as much or as little time reviewing scope and approach as you want, but the default path removes the friction that has constrained application security programs for decades.
Behind that simple request, Cosmos AI orchestrates AI-driven exploration at machine scale, while Bishop Fox's elite security experts validate every finding before it reaches you. You see results as testing progresses in your dashboard, not in a PDF delivered weeks after your engineers have moved on to the next sprint.
Even the authentication setup is simplified. Provide credentials and Cosmos AI navigates login flows, session management, and access controls automatically. No scripted macros. No source code. No configuration overhead pushed onto your security team.
Meeting You Where You Are
The real question is not "what can AI do?" It is "what does your program need AI to do?"
An organization preparing for a SOC 2 audit has very different priorities than one trying to embed security gates into CI/CD pipelines. The metrics that matter, the outcomes that justify investment, and the definition of success all depend on where your program is today and where leadership expects it to be next quarter and next year.
As we think about program maturity, we have found that our customers generally align to one of five stages.
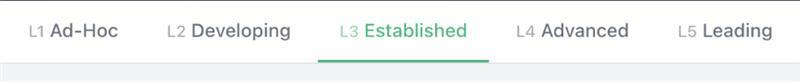
Each stage has distinct goals, distinct metrics, and a distinct way that Cosmos AI delivers value.
When the Goal Is Compliance Readiness
For programs in the early stages, the priority is straightforward: find and fix critical vulnerabilities before the auditor arrives. Success means reducing open critical and highs, meeting remediation of SLAs and demonstrating that applications in scope have been tested.
These teams often have limited budgets and small security staff. Every hour and dollar spent on coordination is time and money not spent on actual testing.
Cosmos AI helps by removing the operational overhead that consumes early-stage program budgets. When you can test more applications at the same cost, you stop making tradeoffs between audit readiness and coverage.
The metric that improves: applications tested per quarter at the same spend, with critical findings surfaced before they become audit failures.
When the Goal Is Coverage Expansion
Once compliance basics are handled, the next challenge is almost always the same: we have 80, 200, or 500 applications and APIs, and we have only tested a fraction of them. Coverage by application tier becomes the key metric. How many Tier 1 crown jewels have been tested this year? What about Tier 2 and Tier 3 applications? How many apps have gone over 12 or 18 months without any testing at all?
This is where the traditional engagement model breaks down completely. You cannot test 200 applications when each one requires weeks of pre-engagement coordination.
Cosmos AI changes the economics. When requesting a test is as simple as submitting a URL, the constraint on coverage is budget, not logistics. Organizations that were testing 30% of their portfolio can realistically target 80% within the same annual spend because the cost per application drops dramatically when you remove the operational overhead.
When the Goal Is Operational Excellence
Programs with solid coverage start optimizing. The metrics shift to mean time to remediate (MTTR), retest pass rates, cost per application, and vendor performance comparison. These teams benchmark everything.
Cosmos AI delivers measurable advantages at this stage because the service model creates a consistent, comparable dataset. These include: time to first validated finding, findings per test, cost per application, and false positive rate. When every finding is expert-validated before delivery, retest pass rates improve because engineering is not wasting cycles on false positives. MTTR drops because findings arrive with actionable reproduction steps and remediation guidance tailored to the customer's stack, not generic OWASP references.
When the Goal Is Pipeline Integration
Advanced programs want security embedded in the development lifecycle. The metrics here reflect that ambition: security gate pass rates, escape rates (vulnerabilities that reach production), time from commit to security feedback, and developer satisfaction with the security process.
This is where most AI-only tools promise the world and fail to deliver. Integrating automated scanning into CI/CD is straightforward. Integrating it in a way that developers actually trust requires findings that are consistently accurate and actionable. A tool with a 20% false positive rate will get turned off by the third sprint. Engineering teams will route around it.
Cosmos AI earns developer trust because every finding has been validated by a human expert before it triggers a security gate. The escape rate drops because testing is comprehensive. The developer experience improves because feedback is reliable. Security stops being the team that cries wolf.
When the Goal Is Proving Security ROI
The most mature programs operate as business functions. They measure security coverage scores, cost per vulnerability found, mean time to detection compared to external sources, and return on security investment. They benchmark against industry peers and produce board-ready reporting on application security posture.
At this stage, Cosmos AI has become a strategic platform. Detection times are measured in days rather than the weeks or months typical of external audits and bug bounty programs. Cost per vulnerability found trends downward as testing scales. A demonstrable ROI connects security spending to avoid business impact and revenue lost. These are the numbers that justify continued investment and demonstrate program maturity to the board.
Why Expert Validation Is Not Optional
Across all five stages of maturity, one principle holds: findings must be trustworthy to drive action.
AI is inherently non-deterministic. It hallucinates. In every other domain, we accept some margin of error. In application security, a false positive is not just noise though; it’s a credibility problem. When security teams deliver findings that turn out to be phantom vulnerabilities, they lose the trust of engineering leadership. Once that trust is gone, security can easily become a checkbox exercise rather than a strategic function.
With Cosmos AI, Bishop Fox experts with years of offensive security experience evaluate every candidate finding before it reaches your team:
- They assess real exploitability in your environment.
- They determine true business severity, not just a CVSS score.
- They verify reproduction steps and provide remediation guidance specific to your technology stack and engineering team’s preferences.
When a finding lands on your dashboard your team can trust it is real, exploitable, and worth fixing. That trust is what enables everything else: faster remediation, developer buy-in, pipeline integration, and board-level confidence in your security posture.
Measuring AI by What Matters
The cybersecurity industry is fixated on AI benchmarks: how many vulnerabilities, how fast, how autonomous. But none of those metrics appear in your board presentation. The questions that matter are the ones your program is already accountable for. Can you test more applications within your budget? Is your mean time to remediate improving? Can you demonstrate ROI on your security investment?
Cosmos AI is built around those questions, providing scale, speed, and coverage that would be impossible with human testers alone. The expert validation ensures that scale translates into trustworthy outcomes rather than a flood of noise, and the service model removes the operational friction that has kept application security programs trapped at their current maturity level.
Security capacity is what matters.
Getting Started
Whether your program is preparing for its next audit or proving security ROI to the board, Cosmos AI meets you where you are and helps you get where you need to go.
Submit a URL. Get validated findings. Move the metrics that matter to your program.
Learn more about Cosmos AI-powered application penetration testing or get started today.
Subscribe to our blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.