



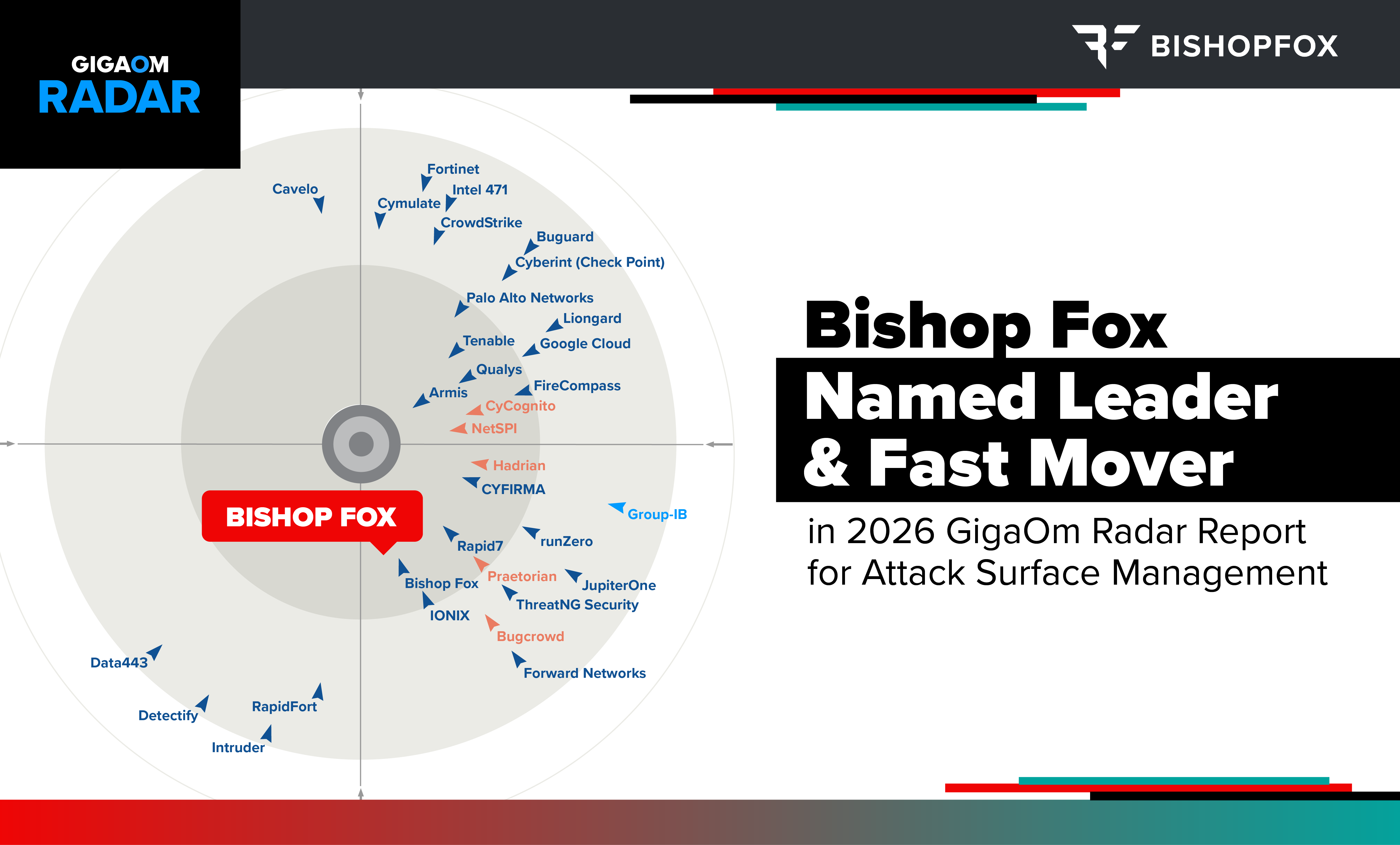
2026 GigaOm Radar for Attack Surface Management
Get an overview of the 2026 Attack Surface Management (ASM) market — along with the key features and business criteria met by the top solutions — and learn why Bishop Fox was named Leader and Fast Mover by the analysts at GigaOm.

Red Team Vendor Evaluation Worksheet
The Red Team Vendor Evaluation Matrix Worksheet is designed to help security leaders evaluate red team vendors thoughtfully before engagement using a structured, question-driven approach.
Application Portfolio Penetration Testing Solution Brief
Download our solution brief. Learn how to secure entire application portfolios with attacker-realistic testing and expert-validated, trusted results.
This site uses cookies to provide you with a great user experience. By continuing to use our website, you consent to the use of cookies. To find out more about the cookies we use, please see our Privacy Policy.